Compliance & Advisory Services
PatientLock offers a broad range of Advisory Services designed for healthcare organizations, including Virtual Chief Information Security Officer (vCISO), NIST CSF and HIPAA Compliance, Security Risk Assessments, HITRUST and SOC2 Readiness, GAP Assessments, and Incident Response (IR).
vCISO
Virtual Chief Information Security Officer (vCISO)
Affordable Security and Compliance Leadership
A Virtual Chief Information Security Officer (vCISO) provides leadership, strategy, and guidance to manage compliance and security risk at a fraction of the cost as compared to hiring a full-time CISO, a position now demanding over $300,000 in salary and benefits each year thanks to a global staffing shortage.
Healthcare organizations should consider vCISO at a fraction of the cost, freeing up budget for other security investments.
vCISO may be best thought of as a world-class, "1099'd security executive" providing oversight in these key areas:
Leadership & Security Strategic Planning
Advising and managing your security risks and strategic plan
Security Awareness Program
Oversight of security awareness and training for your employees
Security Risk Management
Comprehensive risk management, including policies, procedures, and reporting
Security Incident Response
Stay ahead of attacks and minimize impact with immediate assistance
Security Risk Assessment
Planning and implementing your security control frameworks
Security Policy Review
Ongoing checks and balances with security policy review
Corrective Action Plan
Handling security gaps and incidents with a corrective action plan
Security Governance
Advising management and key stakeholders on security governance
Virtual Chief Information Security Officer
Healthcare cybersecurity and compliance can be complex. A full-time CISO is a luxury few organizations can afford, but qualified information security leadership is a must. So, what do you do?
A Virtual Chief Information Security Officer (or vCISO) provides the necessary leadership, strategic planning oversight, and guidance required to achieve compliance and minimize security risk to a healthcare organization.
Virtual Chief Information Security Officer (vCISO)
Affordable Security and Compliance Leadership
A Virtual Chief Information Security Officer (vCISO) provides leadership, strategy, and guidance to manage compliance and security risk at a fraction of the cost as compared to hiring a full-time CISO, a position now demanding over $300,000 in salary and benefits each year thanks to a global staffing shortage.
Healthcare organizations should consider vCISO at a fraction of the cost, freeing up budget for other security investments.
vCISO may be best thought of as a world-class, "1099'd security executive" providing oversight in these key areas:
Leadership & Security Strategic Planning
Advising and managing your security risks and strategic plan
Security Awareness Program
Oversight of security awareness and training for your employees
Security Risk Management
Comprehensive risk management, including policies, procedures, and reporting
Security Incident Response
Stay ahead of attacks and minimize impact with immediate assistance
Security Risk Assessment
Planning and implementing your security control frameworks
Security Policy Review
Ongoing checks and balances with security policy review
Corrective Action Plan
Handling security gaps and incidents with a corrective action plan
Security Governance
Advising management and key stakeholders on security governance
Virtual Chief Information Security Officer (vCISO)
Affordable Security and Compliance Leadership
A Virtual Chief Information Security Officer (vCISO) provides leadership, strategy, and guidance to manage compliance and security risk at a fraction of the cost as compared to hiring a full-time CISO, a position now demanding over $300,000 in salary and benefits each year thanks to a global staffing shortage.
Healthcare organizations should consider vCISO at a fraction of the cost, freeing up budget for other security investments.
vCISO may be best thought of as a world-class, "1099'd security executive" providing oversight in these key areas:
Leadership & Security Strategic Planning
Advising and managing your security risks and strategic plan
Security Awareness Program
Oversight of security awareness and training for your employees
Security Risk Management
Comprehensive risk management, including policies, procedures, and reporting
Security Incident Response
Stay ahead of attacks and minimize impact with immediate assistance
Security Risk Assessment
Planning and implementing your security control frameworks
Security Policy Review
Ongoing checks and balances with security policy review
Corrective Action Plan
Handling security gaps and incidents with a corrective action plan
Security Governance
Advising management and key stakeholders on security governance
Gap / Baseline Assessments
Identify Your Gaps and Roadmap to Compliance
Achieving readiness or certification on a regulation or framework typically involves a gap assessment. We conduct your gap assessment and provide you with a report and remediation roadmap for frameworks & regulations such as ISO 27001, SSAE18 SOC2, PCI-DSS, NIST-CSF, and many more.
NIST Compliance
NIST Cybersecurity Framework:
Gap Assessment & Implementation Support
The National Institute of Standards and Technology (NIST) promotes a Cybersecurity Framework (CSF) to enable organizations to better manage and reduce cybersecurity risk. The framework, which was created through collaboration between industry and government, consists of standards, guidelines, and practices to promote the protection of critical infrastructure. The prioritized, flexible, repeatable, and cost-effective approach of the framework helps owners and operators of critical infrastructure to manage cybersecurity risk. It is also common to use the NIST Cybersecurity Framework to augment regulations like HIPAA to ensure thorough security practices.
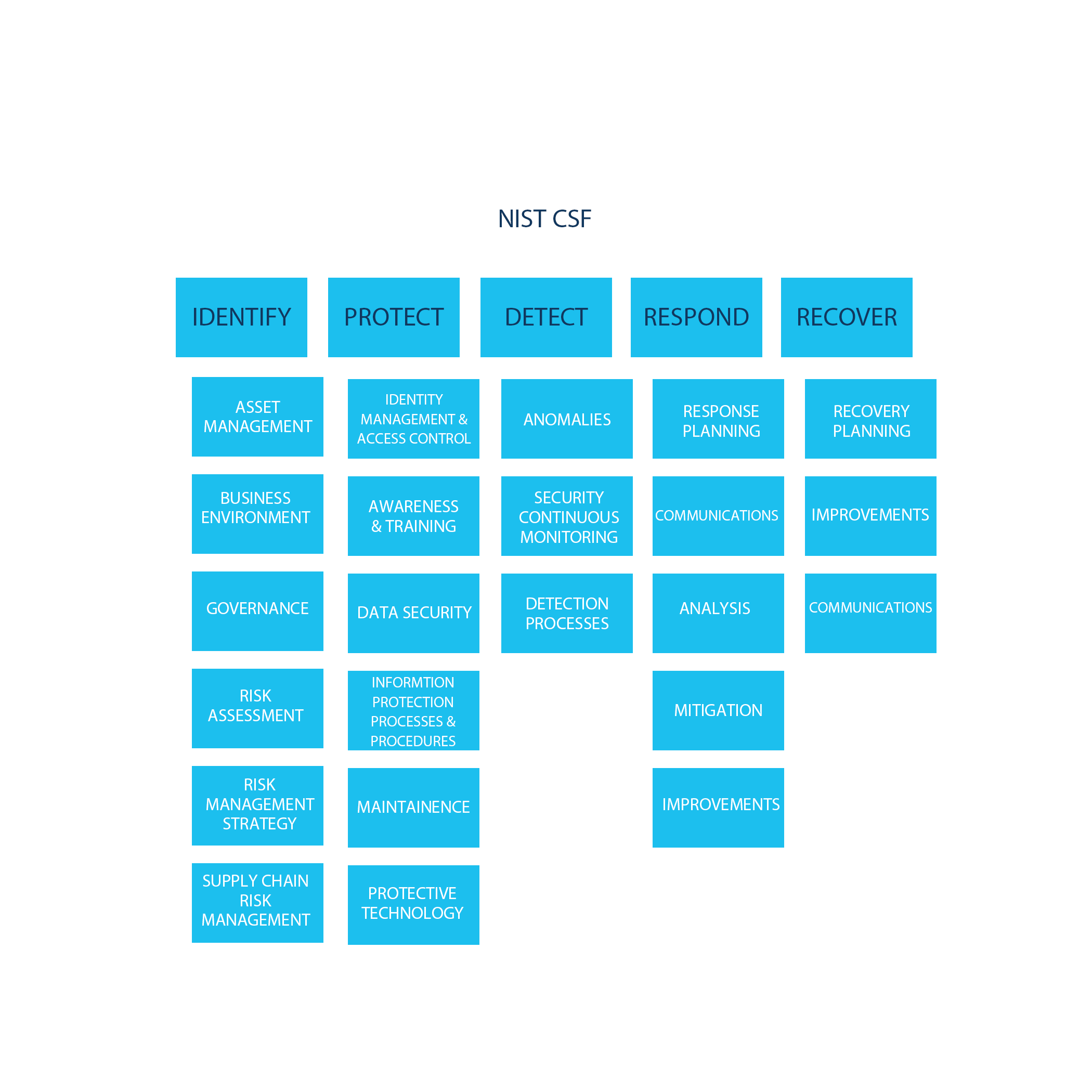
Gap Assessment & Implementation Support
The National Institute of Standards and Technology (NIST) promotes a Cybersecurity Framework (CSF) to enable organizations to better manage and reduce cybersecurity risk.The NIST CSF consists of five core functions – Identify, Protect, Detect, Respond, and Recover. We assess organizations against the five core functions and their categories. This assessment reveals gaps between the framework and the client’s actual security program. Addressing these gaps enables clients improve their cybersecurity posture by implementing a robust, comprehensive cybersecurity framework.
NIST Cybersecurity Framework:
Gap Assessment & Implementation Support
The National Institute of Standards and Technology (NIST) promotes a Cybersecurity Framework (CSF) to enable organizations to better manage and reduce cybersecurity risk. The framework, which was created through collaboration between industry and government, consists of standards, guidelines, and practices to promote the protection of critical infrastructure. The prioritized, flexible, repeatable, and cost-effective approach of the framework helps owners and operators of critical infrastructure to manage cybersecurity risk. It is also common to use the NIST Cybersecurity Framework to augment regulations like HIPAA to ensure thorough security practices.

NIST Cybersecurity Framework:
Gap Assessment & Implementation Support
The National Institute of Standards and Technology (NIST) promotes a Cybersecurity Framework (CSF) to enable organizations to better manage and reduce cybersecurity risk. The framework, which was created through collaboration between industry and government, consists of standards, guidelines, and practices to promote the protection of critical infrastructure. The prioritized, flexible, repeatable, and cost-effective approach of the framework helps owners and operators of critical infrastructure to manage cybersecurity risk. It is also common to use the NIST Cybersecurity Framework to augment regulations like HIPAA to ensure thorough security practices.

PCI Compliance
Painless PCI DSS Compliance
Did you get notified about the v4.0 update?
Falling out of compliance with PCI DSS is a big risk with serious consequences. Monthly fines, fees from banks and payment processors, loss of ability to accept credit cards, liability for fraudulent charges -- even loss of business leading to your business closing.
That’s why PatientLock uses only PCI Qualified Security Assessors (QSA’s) who are certified to conduct assessments against v4.0 of the PCI Data Security Standard.
Take advantage of our expertise to become PCI DSS 4.0 compliant!
PCI DSS Compliance Services
PatientLock follows a comprehensive approach to assess and maintain your PCI DSS compliance and certification. Our highly qualified team with years of experience in this area will take all the necessary steps to ensure your PCI DSS compliance, including:
Review of cardholder data storage locations and formats
Review of access controls
Preparation of Self-Assessment Questionnaire (SAQ) as needed
Assisting towards PCI compliance through the Prioritized Approach Tool
Review of existing agreements, documentation and operating policies and procedures
Developing policies and procedures for payment cards as needed
Payment card process improvement
Security awareness training with specific emphasis on data privacy and managing cardholder data
Developer training on secure programming techniques
Assisting with remediation
Network vulnerability scans
Providing validation of PCI compliance by a certified QSA
Painless Payment Compliance Support
Depending on where you are in your compliance journey, you may be familiar with the Payment Card Industry Data Security Standard (PCI DSS). The PCI DSS is a global standard by the PCI Council that provides a baseline of people, process and technology requirements designated to protect payment data and facilitate consistent data security measures.
PatientLock follows a comprehensive approach to assess and maintain your PCI DSS compliance and certification. Our highly qualified team with years of experience in this area will take the right steps needed to ensure your compliance.
Painless PCI DSS Compliance
Did you get notified about the v4.0 update?
Falling out of compliance with PCI DSS is a big risk with serious consequences. Monthly fines, fees from banks and payment processors, loss of ability to accept credit cards, liability for fraudulent charges -- even loss of business leading to your business closing.
That’s why PatientLock uses only PCI Qualified Security Assessors (QSA’s) who are certified to conduct assessments against v4.0 of the PCI Data Security Standard.
Take advantage of our expertise to become PCI DSS 4.0 compliant!
PCI DSS Compliance Services
PatientLock follows a comprehensive approach to assess and maintain your PCI DSS compliance and certification. Our highly qualified team with years of experience in this area will take all the necessary steps to ensure your PCI DSS compliance, including:
Review of cardholder data storage locations and formats
Review of access controls
Preparation of Self-Assessment Questionnaire (SAQ) as needed
Assisting towards PCI compliance through the Prioritized Approach Tool
Review of existing agreements, documentation and operating policies and procedures
Developing policies and procedures for payment cards as needed
Payment card process improvement
Security awareness training with specific emphasis on data privacy and managing cardholder data
Developer training on secure programming techniques
Assisting with remediation
Network vulnerability scans
Providing validation of PCI compliance by a certified QSA
Painless PCI DSS Compliance
Did you get notified about the v4.0 update?
Falling out of compliance with PCI DSS is a big risk with serious consequences. Monthly fines, fees from banks and payment processors, loss of ability to accept credit cards, liability for fraudulent charges -- even loss of business leading to your business closing.
That’s why PatientLock uses only PCI Qualified Security Assessors (QSA’s) who are certified to conduct assessments against v4.0 of the PCI Data Security Standard.
Take advantage of our expertise to become PCI DSS 4.0 compliant!
PCI DSS Compliance Services
PatientLock follows a comprehensive approach to assess and maintain your PCI DSS compliance and certification. Our highly qualified team with years of experience in this area will take all the necessary steps to ensure your PCI DSS compliance, including:
Review of cardholder data storage locations and formats
Review of access controls
Preparation of Self-Assessment Questionnaire (SAQ) as needed
Assisting towards PCI compliance through the Prioritized Approach Tool
Review of existing agreements, documentation and operating policies and procedures
Developing policies and procedures for payment cards as needed
Payment card process improvement
Security awareness training with specific emphasis on data privacy and managing cardholder data
Developer training on secure programming techniques
Assisting with remediation
Network vulnerability scans
Providing validation of PCI compliance by a certified QSA
CMMC Compliance
CMMC Compliance 2.0
Get Compliant - Schedule Your CMMC 2.0 Gap Assessment
Healthcare organizations looking to apply or maintain partner status with the Department of Defense must have the new CMMC 2.0 certification. Fortunately, PatientLock is experienced working with organizations in the Defense Industrial Base on their journey to CMMC compliance.
CMMC 2.0 Services
To ensure you remain qualified as a DoD contract bidder, PatientLock walks you through every step with the following pre-certification efforts:
Assess
Perform a gap assessment to determine your current state of compliance with the CMMC and NIST SP 800-171 requirements
Assist
System Security Plan (SSP) and Plan of Action and Milestones (POA&M) to address any gaps
Advise
Advisory assistance with remediation efforts and tracking milestones against the POA&M
Implement
Vulnerability assessments, penetration testing—and other services as may be required
Create
Technology, processes, and policies and procedures internally or for projects with external IT vendors (MSPs/ MSSPs)
Get Ready for CMMC 2.0 Compliance
PatientLock provides CMMC readiness services to healthcare organizations on their path to certification against the CMMC standard.
CMMC Compliance 2.0
Get Compliant - Schedule Your CMMC 2.0 Gap Assessment
Healthcare organizations looking to apply or maintain partner status with the Department of Defense must have the new CMMC 2.0 certification. Fortunately, PatientLock is experienced working with organizations in the Defense Industrial Base on their journey to CMMC compliance.
CMMC 2.0 Services
To ensure you remain qualified as a DoD contract bidder, PatientLock walks you through every step with the following pre-certification efforts:
Assess
Perform a gap assessment to determine your current state of compliance with the CMMC and NIST SP 800-171 requirements
Assist
System Security Plan (SSP) and Plan of Action and Milestones (POA&M) to address any gaps
Advise
Advisory assistance with remediation efforts and tracking milestones against the POA&M
Implement
Vulnerability assessments, penetration testing—and other services as may be required
Create
Technology, processes, and policies and procedures internally or for projects with external IT vendors (MSPs/ MSSPs)
CMMC Compliance 2.0
Get Compliant - Schedule Your CMMC 2.0 Gap Assessment
Healthcare organizations looking to apply or maintain partner status with the Department of Defense must have the new CMMC 2.0 certification. Fortunately, PatientLock is experienced working with organizations in the Defense Industrial Base on their journey to CMMC compliance.
CMMC 2.0 Services
To ensure you remain qualified as a DoD contract bidder, PatientLock walks you through every step with the following pre-certification efforts:
Assess
Perform a gap assessment to determine your current state of compliance with the CMMC and NIST SP 800-171 requirements
Assist
System Security Plan (SSP) and Plan of Action and Milestones (POA&M) to address any gaps
Advise
Advisory assistance with remediation efforts and tracking milestones against the POA&M
Implement
Vulnerability assessments, penetration testing—and other services as may be required
Create
Technology, processes, and policies and procedures internally or for projects with external IT vendors (MSPs/ MSSPs)
HIPAA Risk Assessment
HIPAA Compliance Just Got Easier
Get Your Annual HIPAA Risk Assessment
PatientLock walks you through every step of the HIPAA process, from assessment to implementation and maintenance, telling you exactly what you need to meet expectations. Find out why hundreds of healthcare organizations trust PatientLock for HIPAA Compliance.
Take the first step and schedule your initial consultation with us at no cost to you.
HIPAA Compliance Services
Our team of cybersecurity and compliance experts simplify HIPAA compliance into a few key steps — saving you time and limiting employee stress while making sure you stay compliant.
Assess
HIPAA risk assessment and gap analysis
Create
HIPAA compliant privacy and security policies
Train
Employees on Cybersecurity and HIPAA practices
Monitor
HIPAA Compliance Just Got Easier
PatientLock walks you through every step of the HIPAA process, from assessment to implementation and maintenance, telling you exactly what you need to meet expectations. Find out why hundreds of healthcare organizations trust our HIPAA Compliance services.
Our team of cybersecurity and compliance experts simplify HIPAA compliance into a few key steps — saving you time and limiting employee stress while making sure you stay compliant.
HIPAA Compliance Just Got Easier
Get Your Annual HIPAA Risk Assessment
PatientLock walks you through every step of the HIPAA process, from assessment to implementation and maintenance, telling you exactly what you need to meet expectations. Find out why hundreds of healthcare organizations trust PatientLock for HIPAA Compliance.
Take the first step and schedule your initial consultation with us at no cost to you.
HIPAA Compliance Services
Our team of cybersecurity and compliance experts simplify HIPAA compliance into a few key steps — saving you time and limiting employee stress while making sure you stay compliant.
Assess
HIPAA risk assessment and gap analysis
Create
HIPAA compliant privacy and security policies
Train
Employees on Cybersecurity and HIPAA practices
Monitor
HIPAA Compliance Just Got Easier
Get Your Annual HIPAA Risk Assessment
PatientLock walks you through every step of the HIPAA process, from assessment to implementation and maintenance, telling you exactly what you need to meet expectations. Find out why hundreds of healthcare organizations trust PatientLock for HIPAA Compliance.
Take the first step and schedule your initial consultation with us at no cost to you.
HIPAA Compliance Services
Our team of cybersecurity and compliance experts simplify HIPAA compliance into a few key steps — saving you time and limiting employee stress while making sure you stay compliant.
Assess
HIPAA risk assessment and gap analysis
Create
HIPAA compliant privacy and security policies
Train
Employees on Cybersecurity and HIPAA practices
Monitor
Incident Response (IR)
Incident Response Planning
Be Prepared for Your Next Cyber Incident
Incident response is the systematic approach in which an organization handles a cyber incident or a breach. At a minimum, every organization must have a clear and comprehensive incident response plan outlining roles and responsibilities, process and procedures in the event of a cyber incident. Every person involved in executing the incident response must be trained and should have participated in a series of tests of the plan.
Be Prepared for Your Next Cyber Incident
Incident response is the systematic approach in which an organization handles a cyber incident or a breach. At a minimum, every organization must have a clear and comprehensive incident response plan outlining roles and responsibilities, process and procedures in the event of a cyber incident. Every person involved in executing the incident response must be trained and should have participated in a series of tests of the plan.
PatientLock is your trusted partner in incident response planning and testing. We work with you in the end-to-end process for incident response.
Incident Response Planning
Be Prepared for Your Next Cyber Incident

Incident response is the systematic approach in which an organization handles a cyber incident or a breach. At a minimum, every organization must have a clear and comprehensive incident response plan outlining roles and responsibilities, process and procedures in the event of a cyber incident. Every person involved in executing the incident response must be trained and should have participated in a series of tests of the plan.
Incident Response Planning
Be Prepared for Your Next Cyber Incident

Incident response is the systematic approach in which an organization handles a cyber incident or a breach. At a minimum, every organization must have a clear and comprehensive incident response plan outlining roles and responsibilities, process and procedures in the event of a cyber incident. Every person involved in executing the incident response must be trained and should have participated in a series of tests of the plan.
HITRUST Readiness
Your Partner in HITRUST Readiness
HITRUST Readiness Services
We offer readiness services for HITRUST CSF v11 at all three levels, including e1, i1, and r2.
Our HITRUST Readiness Services include:
Assistance in determining which level of security assurance and certification is most suitable for your organization, and the controls and requirements to be implemented for that level.
Assistance in implementing the CSF Framework for the security assurance level you have chosen, identifying compliance gaps, and remediating those gaps until all requirements are met.
Preparation of policies, procedures, reports, and other documentation required by the CSF Framework.
Preparation of policies, procedures, reports, and other documentation required by the CSF Framework.
Assistance in addressing remaining activities that may be required to achieve applicable industry-specific compliance.
Ongoing maintenance to prevent erosion of compliance over time, as may occur with the introduction or retirement of technology, systems, infrastructure, or key personnel.
HITRUST CSF Framework Readiness Service
Achieve your objective in a timely and efficient manner with PatientLock’s HITRUST Readiness Services.
PatientLock will walk you through a Readiness Assessment for the HITRUST CSF Framework, remediate the gaps, and prepare for a successful, certifiable HITRUST Assessment.
HITRUST Readiness is designed to help you achieve HITRUST CSF Framework validation and compliance with regulatory requirements applicable to healthcare organizations.
Your Partner in HITRUST Readiness
HITRUST Readiness Services
We offer readiness services for HITRUST CSF v11 at all three levels, including e1, i1, and r2.
Our HITRUST Readiness Services include:
Assistance in determining which level of security assurance and certification is most suitable for your organization, and the controls and requirements to be implemented for that level.
Assistance in implementing the CSF Framework for the security assurance level you have chosen, identifying compliance gaps, and remediating those gaps until all requirements are met.
Preparation of policies, procedures, reports, and other documentation required by the CSF Framework.
Preparation of policies, procedures, reports, and other documentation required by the CSF Framework.
Assistance in addressing remaining activities that may be required to achieve applicable industry-specific compliance.
Ongoing maintenance to prevent erosion of compliance over time, as may occur with the introduction or retirement of technology, systems, infrastructure, or key personnel.
Your Partner in HITRUST Readiness
HITRUST Readiness Services
We offer readiness services for HITRUST CSF v11 at all three levels, including e1, i1, and r2.
Our HITRUST Readiness Services include:
Assistance in determining which level of security assurance and certification is most suitable for your organization, and the controls and requirements to be implemented for that level.
Assistance in implementing the CSF Framework for the security assurance level you have chosen, identifying compliance gaps, and remediating those gaps until all requirements are met.
Preparation of policies, procedures, reports, and other documentation required by the CSF Framework.
Preparation of policies, procedures, reports, and other documentation required by the CSF Framework.
Assistance in addressing remaining activities that may be required to achieve applicable industry-specific compliance.
Ongoing maintenance to prevent erosion of compliance over time, as may occur with the introduction or retirement of technology, systems, infrastructure, or key personnel.
Penetration Testing
Penetration Testing
What is Penetration Testing?
Penetration testing is an IT security process where a skilled human resource simulates an authorized attack on a system with its primary goal being to identify any vulnerabilities. In recent years, as the online economy transformed both business and society, the need for this type of service has emerged as a requirement for organizations of all sizes. A penetration test takes a holistic look at your organization’s security through the eyes of an attacker. The process forms part of a security risk assessment, which includes activities such as identifying vulnerabilities in your IT environment, web application testing, and assessing the state of your staff’s security awareness with simulated social engineering attacks.
Modern organizations are entirely dependent on technology to operate effectively, and the information they produce and store on their IT infrastructure has grown into a business asset which holds intrinsic value. The digital age has spawned a new type of criminal, one which is intent on breaking into systems and stealing data. Penetration testing was created to simulate this criminal activity and help businesses find any weaknesses and implement remedies before a hacker could exploit them. However, is penetration testing an essential practice for every organization and what are the benefits and drawbacks of undertaking such an exercise?
Does My Organization Need Penetration Testing?
No organization is immune from a cyber attack. Even though big names make the news when they are the victims of a hack, small businesses are the most common victims of data breaches according to the Verizon 2018 Data Breach Investigations Report. Consequently, penetration testing is no longer a recommendation, but a necessity for every organization which operates online, and in some instances, is a condition to achieve compliance.
The Payment Card Industry Data Security Standard (PCI-DSS) mandates under requirement 11.3 that organizations which store and process card payments must regularly perform penetration tests to identify possible security issues. Other regulatory frameworks, such as the European Union’s General Data Protection Regulation (GDPR), do not explicitly state that penetration tests are mandatory. They do however require organizations to assess their applications and critical infrastructure for security vulnerabilities regularly. As such, every business which needs to meet specific compliance requirements must include penetration testing as part of their IT security framework.
The Pros of Penetration Testing
Introduces a Proactive Human Element
There are many advantages which organizations derive from conducting regular penetration tests on their IT environment. The most significant benefit is that it introduces a proactive human element into an organization’s cybersecurity structure. By immersing themselves into an attacker’s mindset, penetration testers gain a unique perspective on an organization’s existing IT defenses. This point of view places them in an exceptional position to identify potential vulnerabilities specific to the organization which automated vulnerability scans often miss.
Tailored to Meet Your Unique Needs
Every organization is unique, and penetration testers take this into account when conducting their assessment. Although modern vulnerability scanners can detect a myriad of vulnerabilities in known systems, these generic solutions often miss potential issues which are business specific. A skilled penetration tester may use automated tools but will supplement these with real-world skill and experience ensuring a holistic approach. By tailoring their assessment to meet the unique needs of each organization, the tester can uncover issues which are specific to the organization under review.
Holistic Approach Can Identify High-Risk Vulnerabilities
Modern automated vulnerability scanners often detect a myriad of low-risk vulnerabilities in any IT infrastructure. In isolation, these risks may seem negligible and pose no real threat to the business. However, the combination of a few of these identified weaknesses could well represent a significant risk if an attacker exploits them in a particular sequence. Automated vulnerability scans lack the intelligence to make these connections. However, a skilled penetration tester can identify this deficiency as their talent and experience give them the human ability to connect the dots.
Provides Specific Advice
The final stage in any professional penetration test is the submission of a report with findings and recommendations. Unlike automated tools which provide general fixes, a document written by a skilled penetration tester will offer specific suggestions created to remedy the particular weaknesses they uncovered during their assessment.
Helping Identify and Remediate Vulnerabilities
Penetration testing is an IT security process where a skilled human resource simulates an authorized attack on a system with its primary goal being to identify any vulnerabilities.
Protecting your organization from cybersecurity threats requires you to take a proactive approach. Healthcare Organizations are prime targets for cyber criminals as the most recent data breach statistics have shown. Penetration testing is a proactive security process which introduces the human element needed in today’s current threat environment. It takes a holistic approach and is tailored to the unique needs of each organization.
Penetration Testing
What is Penetration Testing?
Penetration testing is an IT security process where a skilled human resource simulates an authorized attack on a system with its primary goal being to identify any vulnerabilities. In recent years, as the online economy transformed both business and society, the need for this type of service has emerged as a requirement for organizations of all sizes. A penetration test takes a holistic look at your organization’s security through the eyes of an attacker. The process forms part of a security risk assessment, which includes activities such as identifying vulnerabilities in your IT environment, web application testing, and assessing the state of your staff’s security awareness with simulated social engineering attacks.
Modern organizations are entirely dependent on technology to operate effectively, and the information they produce and store on their IT infrastructure has grown into a business asset which holds intrinsic value. The digital age has spawned a new type of criminal, one which is intent on breaking into systems and stealing data. Penetration testing was created to simulate this criminal activity and help businesses find any weaknesses and implement remedies before a hacker could exploit them. However, is penetration testing an essential practice for every organization and what are the benefits and drawbacks of undertaking such an exercise?
Does My Organization Need Penetration Testing?
No organization is immune from a cyber attack. Even though big names make the news when they are the victims of a hack, small businesses are the most common victims of data breaches according to the Verizon 2018 Data Breach Investigations Report. Consequently, penetration testing is no longer a recommendation, but a necessity for every organization which operates online, and in some instances, is a condition to achieve compliance.
The Payment Card Industry Data Security Standard (PCI-DSS) mandates under requirement 11.3 that organizations which store and process card payments must regularly perform penetration tests to identify possible security issues. Other regulatory frameworks, such as the European Union’s General Data Protection Regulation (GDPR), do not explicitly state that penetration tests are mandatory. They do however require organizations to assess their applications and critical infrastructure for security vulnerabilities regularly. As such, every business which needs to meet specific compliance requirements must include penetration testing as part of their IT security framework.
The Pros of Penetration Testing
Introduces a Proactive Human Element
There are many advantages which organizations derive from conducting regular penetration tests on their IT environment. The most significant benefit is that it introduces a proactive human element into an organization’s cybersecurity structure. By immersing themselves into an attacker’s mindset, penetration testers gain a unique perspective on an organization’s existing IT defenses. This point of view places them in an exceptional position to identify potential vulnerabilities specific to the organization which automated vulnerability scans often miss.
Tailored to Meet Your Unique Needs
Every organization is unique, and penetration testers take this into account when conducting their assessment. Although modern vulnerability scanners can detect a myriad of vulnerabilities in known systems, these generic solutions often miss potential issues which are business specific. A skilled penetration tester may use automated tools but will supplement these with real-world skill and experience ensuring a holistic approach. By tailoring their assessment to meet the unique needs of each organization, the tester can uncover issues which are specific to the organization under review.
Holistic Approach Can Identify High-Risk Vulnerabilities
Modern automated vulnerability scanners often detect a myriad of low-risk vulnerabilities in any IT infrastructure. In isolation, these risks may seem negligible and pose no real threat to the business. However, the combination of a few of these identified weaknesses could well represent a significant risk if an attacker exploits them in a particular sequence. Automated vulnerability scans lack the intelligence to make these connections. However, a skilled penetration tester can identify this deficiency as their talent and experience give them the human ability to connect the dots.
Provides Specific Advice
The final stage in any professional penetration test is the submission of a report with findings and recommendations. Unlike automated tools which provide general fixes, a document written by a skilled penetration tester will offer specific suggestions created to remedy the particular weaknesses they uncovered during their assessment.
Penetration Testing
What is Penetration Testing?
Penetration testing is an IT security process where a skilled human resource simulates an authorized attack on a system with its primary goal being to identify any vulnerabilities. In recent years, as the online economy transformed both business and society, the need for this type of service has emerged as a requirement for organizations of all sizes. A penetration test takes a holistic look at your organization’s security through the eyes of an attacker. The process forms part of a security risk assessment, which includes activities such as identifying vulnerabilities in your IT environment, web application testing, and assessing the state of your staff’s security awareness with simulated social engineering attacks.
Modern organizations are entirely dependent on technology to operate effectively, and the information they produce and store on their IT infrastructure has grown into a business asset which holds intrinsic value. The digital age has spawned a new type of criminal, one which is intent on breaking into systems and stealing data. Penetration testing was created to simulate this criminal activity and help businesses find any weaknesses and implement remedies before a hacker could exploit them. However, is penetration testing an essential practice for every organization and what are the benefits and drawbacks of undertaking such an exercise?
Does My Organization Need Penetration Testing?
No organization is immune from a cyber attack. Even though big names make the news when they are the victims of a hack, small businesses are the most common victims of data breaches according to the Verizon 2018 Data Breach Investigations Report. Consequently, penetration testing is no longer a recommendation, but a necessity for every organization which operates online, and in some instances, is a condition to achieve compliance.
The Payment Card Industry Data Security Standard (PCI-DSS) mandates under requirement 11.3 that organizations which store and process card payments must regularly perform penetration tests to identify possible security issues. Other regulatory frameworks, such as the European Union’s General Data Protection Regulation (GDPR), do not explicitly state that penetration tests are mandatory. They do however require organizations to assess their applications and critical infrastructure for security vulnerabilities regularly. As such, every business which needs to meet specific compliance requirements must include penetration testing as part of their IT security framework.
The Pros of Penetration Testing
Introduces a Proactive Human Element
There are many advantages which organizations derive from conducting regular penetration tests on their IT environment. The most significant benefit is that it introduces a proactive human element into an organization’s cybersecurity structure. By immersing themselves into an attacker’s mindset, penetration testers gain a unique perspective on an organization’s existing IT defenses. This point of view places them in an exceptional position to identify potential vulnerabilities specific to the organization which automated vulnerability scans often miss.
Tailored to Meet Your Unique Needs
Every organization is unique, and penetration testers take this into account when conducting their assessment. Although modern vulnerability scanners can detect a myriad of vulnerabilities in known systems, these generic solutions often miss potential issues which are business specific. A skilled penetration tester may use automated tools but will supplement these with real-world skill and experience ensuring a holistic approach. By tailoring their assessment to meet the unique needs of each organization, the tester can uncover issues which are specific to the organization under review.
Holistic Approach Can Identify High-Risk Vulnerabilities
Modern automated vulnerability scanners often detect a myriad of low-risk vulnerabilities in any IT infrastructure. In isolation, these risks may seem negligible and pose no real threat to the business. However, the combination of a few of these identified weaknesses could well represent a significant risk if an attacker exploits them in a particular sequence. Automated vulnerability scans lack the intelligence to make these connections. However, a skilled penetration tester can identify this deficiency as their talent and experience give them the human ability to connect the dots.
Provides Specific Advice
The final stage in any professional penetration test is the submission of a report with findings and recommendations. Unlike automated tools which provide general fixes, a document written by a skilled penetration tester will offer specific suggestions created to remedy the particular weaknesses they uncovered during their assessment.
Network Security Assessment
Comprehensive Network Analysis
Network Security Assessments are a critical component of maintaining the integrity and confidentiality of your organization’s data and assets. Our team of experts will perform a thorough analysis of your network infrastructure, identifying any potential weaknesses or vulnerabilities. This includes examining your firewalls, routers, switches, and other networking devices to ensure they are properly configured and protected against external threats.
Proactively mitigate risks and protect your business from cyberattacks, data breaches, and other security incidents. Our assessment report will provide recommendations for improving your network security, and our team will work with you to implement these changes and ensure your network is secure.
vCISO
Virtual Chief Information Security Officer
Healthcare cybersecurity and compliance can be complex. A full-time CISO is a luxury few organizations can afford, but qualified information security leadership is a must. So, what do you do?
A Virtual Chief Information Security Officer (or vCISO) provides the necessary leadership, strategic planning oversight, and guidance required to achieve compliance and minimize security risk to a healthcare organization.
Gap / Baseline Assessments
Identify Your Gaps and Roadmap to Compliance
Achieving readiness or certification on a regulation or framework typically involves a gap assessment. We conduct your gap assessment and provide you with a report and remediation roadmap for frameworks & regulations such as ISO 27001, SSAE18 SOC2, PCI-DSS, NIST-CSF, and many more.
NIST Compliance
Gap Assessment & Implementation Support
The National Institute of Standards and Technology (NIST) promotes a Cybersecurity Framework (CSF) to enable organizations to better manage and reduce cybersecurity risk.The NIST CSF consists of five core functions – Identify, Protect, Detect, Respond, and Recover. We assess organizations against the five core functions and their categories. This assessment reveals gaps between the framework and the client’s actual security program. Addressing these gaps enables clients improve their cybersecurity posture by implementing a robust, comprehensive cybersecurity framework.
PCI Compliance
Painless Payment Compliance Support
Depending on where you are in your compliance journey, you may be familiar with the Payment Card Industry Data Security Standard (PCI DSS). The PCI DSS is a global standard by the PCI Council that provides a baseline of people, process and technology requirements designated to protect payment data and facilitate consistent data security measures.
PatientLock follows a comprehensive approach to assess and maintain your PCI DSS compliance and certification. Our highly qualified team with years of experience in this area will take the right steps needed to ensure your compliance.
CMMC Compliance
Get Ready for CMMC 2.0 Compliance
PatientLock provides CMMC readiness services to healthcare organizations on their path to certification against the CMMC standard.
HIPAA Risk Assessment
HIPAA Compliance Just Got Easier
PatientLock walks you through every step of the HIPAA process, from assessment to implementation and maintenance, telling you exactly what you need to meet expectations. Find out why hundreds of healthcare organizations trust our HIPAA Compliance services.
Our team of cybersecurity and compliance experts simplify HIPAA compliance into a few key steps — saving you time and limiting employee stress while making sure you stay compliant.
Incident Response (IR)
Be Prepared for Your Next Cyber Incident
Incident response is the systematic approach in which an organization handles a cyber incident or a breach. At a minimum, every organization must have a clear and comprehensive incident response plan outlining roles and responsibilities, process and procedures in the event of a cyber incident. Every person involved in executing the incident response must be trained and should have participated in a series of tests of the plan.
PatientLock is your trusted partner in incident response planning and testing. We work with you in the end-to-end process for incident response.
HITRUST Readiness
HITRUST CSF Framework Readiness Service
Achieve your objective in a timely and efficient manner with PatientLock’s HITRUST Readiness Services.
PatientLock will walk you through a Readiness Assessment for the HITRUST CSF Framework, remediate the gaps, and prepare for a successful, certifiable HITRUST Assessment.
HITRUST Readiness is designed to help you achieve HITRUST CSF Framework validation and compliance with regulatory requirements applicable to healthcare organizations.
Penetration Testing
Helping Identify and Remediate Vulnerabilities
Penetration testing is an IT security process where a skilled human resource simulates an authorized attack on a system with its primary goal being to identify any vulnerabilities.
Protecting your organization from cybersecurity threats requires you to take a proactive approach. Healthcare Organizations are prime targets for cyber criminals as the most recent data breach statistics have shown. Penetration testing is a proactive security process which introduces the human element needed in today’s current threat environment. It takes a holistic approach and is tailored to the unique needs of each organization.
Network Security Assessment
Comprehensive Network Analysis
Network Security Assessments are a critical component of maintaining the integrity and confidentiality of your organization’s data and assets. Our team of experts will perform a thorough analysis of your network infrastructure, identifying any potential weaknesses or vulnerabilities. This includes examining your firewalls, routers, switches, and other networking devices to ensure they are properly configured and protected against external threats.
Proactively mitigate risks and protect your business from cyberattacks, data breaches, and other security incidents. Our assessment report will provide recommendations for improving your network security, and our team will work with you to implement these changes and ensure your network is secure.
