Cybersecurity Services
Leveraging the same People, Process, and DARPA-born security Technologies protecting global defense-contractors, the DOD, and over 4,000 clients in highly targeted sectors, PatientLock makes enterprise-grade cybersecurity affordable and accessible to any size of healthcare organization.
24/7/365 Security Operations Center
24/7/365 SOC Monitoring
Around-the-Clock Threat Protection
Healthcare regulators are under increasing pressure to update and enforce framework regulations like NIST, HIPAA, and PCI-DSS. Cyber insurance policies are now starting to require 24/7 monitoring services, commonly seen as "SOC monitoring", "SIEM", or "MDR" on insurance applications.
For most organizations, this creates uncertainty about existing safeguards being adequate, and also raises compliance concerns. More technology means more staffing required to implement, manage, and monitor them. Unfortunately, a global staffing shortage in Information Security means those people don't exist, and, they'd be too expensive for most healthcare organizations to hire if they did.
Cyber criminals funded by adversarial nation-states continue to develop new and sophisticated ways to breach healthcare data systems. Regulatory sanctions and fines, coupled with potential financial losses from an attack and the subsequent reputational damage has cybersecurity front-and-center.
PatientLock addresses those concerns by examining data from individual devices and correlating the information across the broader set of feeds, while analysts in our 24x7x365 SOC detect and neutralize threats before they can impact your business.
Benefits of
PatientLock Security Monitoring
Around-the-clock security coverage without hiring IT or IS staff.
Streamlined communication between our SOC security talent and key stakeholders in healthcare organizations.
24x7x365 active monitoring meets the requirements of healthcare regulatory compliance guidelines, as well as cyber insurance requirements.
PatientLock's security staff works as an extension of your business, enabling any size of healthcare organization to have a world-class cybersecurity and compliance program without the need for additional staffing or technology acquisition.
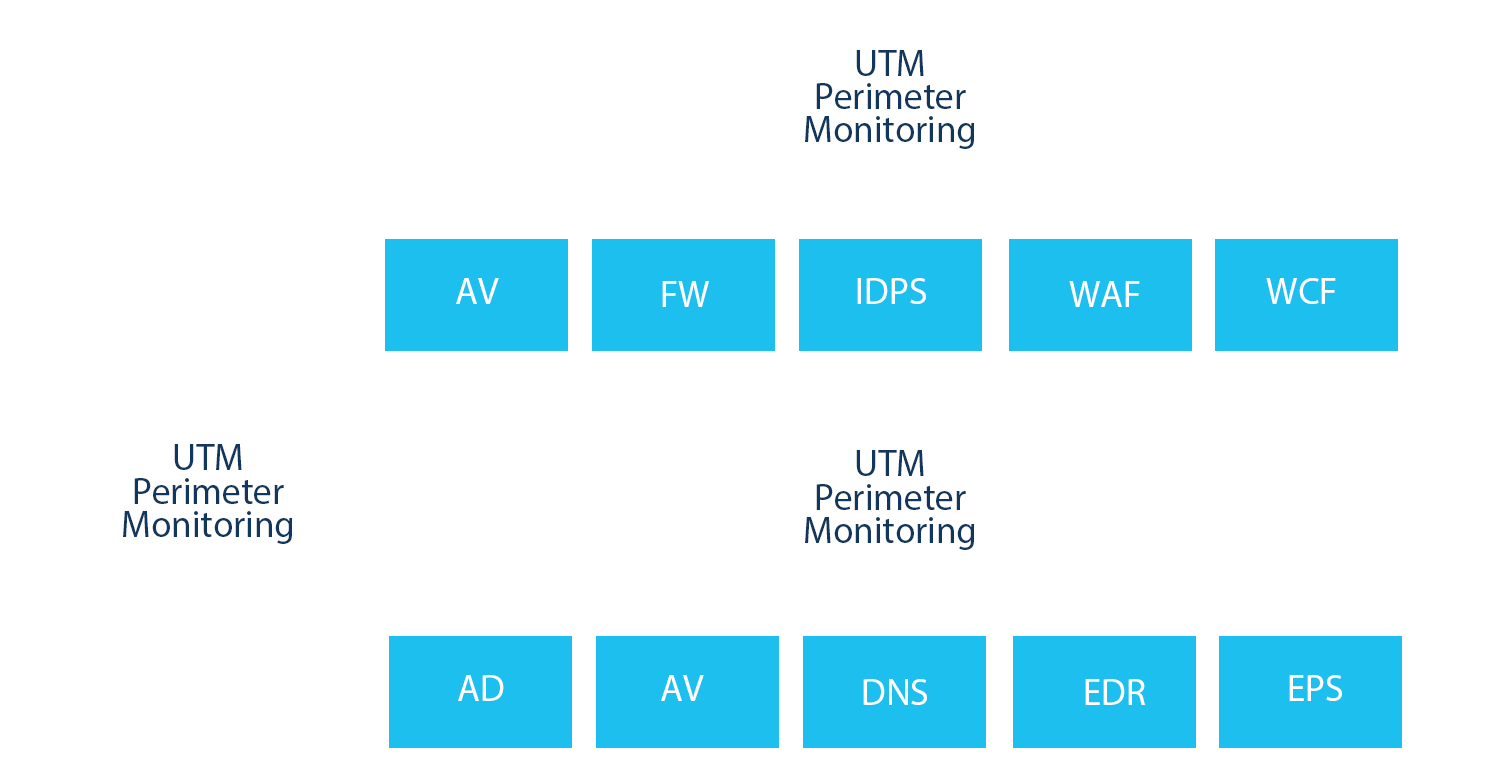
SOC Monitoring is critical to compliance
A lynchpin of cybersecurity best-practice frameworks and regulatory compliance is active monitoring of networks, systems, and endpoints. For example, NIST, ISO 27001, GLBA, FFIEC, HIPAA, PCI DSS, NYDFS, CCPA and many others highlight the need for active monitoring.
PatientLock’s Security Monitoring offers both perimeter and extended monitoring to make sure your organization and patients are safe, and your compliance requirements are met.
Enterprise-class monitoring at an affordable price
With today’s threat landscape and risk to healthcare organizations, monitoring the perimeter with a firewall is no longer enough. Organizations of all sizes need to monitor all points in their clinic, hospital, or healthcare related business. That means networks, servers, databases, people, connected medical devices, and traditional endpoints.
That’s a challenge for already strained IT (or IS) resources.
PatientLock solves that challenge by acting as a force multiplier to a healthcare organization’s security staff by monitoring network assets, 24x7x365. PatientLock monitors your environment around-the-clock, neutralizing threats before they can impact your business or patients.
24/7/365 SOC Monitoring
Around-the-Clock Threat Protection
Healthcare regulators are under increasing pressure to update and enforce framework regulations like NIST, HIPAA, and PCI-DSS. Cyber insurance policies are now starting to require 24/7 monitoring services, commonly seen as "SOC monitoring", "SIEM", or "MDR" on insurance applications.
For most organizations, this creates uncertainty about existing safeguards being adequate, and also raises compliance concerns. More technology means more staffing required to implement, manage, and monitor them. Unfortunately, a global staffing shortage in Information Security means those people don't exist, and, they'd be too expensive for most healthcare organizations to hire if they did.
Cyber criminals funded by adversarial nation-states continue to develop new and sophisticated ways to breach healthcare data systems. Regulatory sanctions and fines, coupled with potential financial losses from an attack and the subsequent reputational damage has cybersecurity front-and-center.
PatientLock addresses those concerns by examining data from individual devices and correlating the information across the broader set of feeds, while analysts in our 24x7x365 SOC detect and neutralize threats before they can impact your business.
Benefits of
PatientLock Security Monitoring
Around-the-clock security coverage without hiring IT or IS staff.
Streamlined communication between our SOC security talent and key stakeholders in healthcare organizations.
24x7x365 active monitoring meets the requirements of healthcare regulatory compliance guidelines, as well as cyber insurance requirements.
PatientLock's security staff works as an extension of your business, enabling any size of healthcare organization to have a world-class cybersecurity and compliance program without the need for additional staffing or technology acquisition.

SOC Monitoring is critical to compliance
A lynchpin of cybersecurity best-practice frameworks and regulatory compliance is active monitoring of networks, systems, and endpoints. For example, NIST, ISO 27001, GLBA, FFIEC, HIPAA, PCI DSS, NYDFS, CCPA and many others highlight the need for active monitoring.
PatientLock’s Security Monitoring offers both perimeter and extended monitoring to make sure your organization and patients are safe, and your compliance requirements are met.
24/7/365 SOC Monitoring
Around-the-Clock Threat Protection
Healthcare regulators are under increasing pressure to update and enforce framework regulations like NIST, HIPAA, and PCI-DSS. Cyber insurance policies are now starting to require 24/7 monitoring services, commonly seen as "SOC monitoring", "SIEM", or "MDR" on insurance applications.
For most organizations, this creates uncertainty about existing safeguards being adequate, and also raises compliance concerns. More technology means more staffing required to implement, manage, and monitor them. Unfortunately, a global staffing shortage in Information Security means those people don't exist, and, they'd be too expensive for most healthcare organizations to hire if they did.
Cyber criminals funded by adversarial nation-states continue to develop new and sophisticated ways to breach healthcare data systems. Regulatory sanctions and fines, coupled with potential financial losses from an attack and the subsequent reputational damage has cybersecurity front-and-center.
PatientLock addresses those concerns by examining data from individual devices and correlating the information across the broader set of feeds, while analysts in our 24x7x365 SOC detect and neutralize threats before they can impact your business.
Benefits of
PatientLock Security Monitoring
Around-the-clock security coverage without hiring IT or IS staff.
Streamlined communication between our SOC security talent and key stakeholders in healthcare organizations.
24x7x365 active monitoring meets the requirements of healthcare regulatory compliance guidelines, as well as cyber insurance requirements.
PatientLock's security staff works as an extension of your business, enabling any size of healthcare organization to have a world-class cybersecurity and compliance program without the need for additional staffing or technology acquisition.

SOC Monitoring is critical to compliance
A lynchpin of cybersecurity best-practice frameworks and regulatory compliance is active monitoring of networks, systems, and endpoints. For example, NIST, ISO 27001, GLBA, FFIEC, HIPAA, PCI DSS, NYDFS, CCPA and many others highlight the need for active monitoring.
PatientLock’s Security Monitoring offers both perimeter and extended monitoring to make sure your organization and patients are safe, and your compliance requirements are met.
Extended Detection and Response (XDR)
Extended Detection and Response (XDR)
For Those About to SOC
Reduce the time to detect and respond to threats in your environment.
Despite your organization’s best efforts, threats can break through your security defenses. And when they do, you need to stop them fast, before they can cause damage.
A security information event management (SIEM) tool is foundational to the visibility and context that fuel effective threat detection and response. A SIEM collects and consolidates security data from devices across your modern distributed environment and normalizes it so that it can be analyzed and monitored for threats.
Managing a SIEM in-house requires staffing, yet an industry talent shortage is underscored by the constantly evolving threats to your business.
Misconfiguration is common and can result in the SIEM generating excessive false alerts, which mask real threats. Not to mention, a SIEM alone can’t tell you how to respond to an alert.
With PatientLock Managed SIEM, you get all the advantages of a SIEM without the complexity.
A SIEM can help you detect and respond to threats in your environment before they can cause damage to your business or patients. PatientLock Managed SIEM offers flexible service levels that can take over wherever your internal team’s bandwidth or skills leave off. Whether you have your own instance of FortiSIEM or use ours, PatientLock skilled analysts and engineers work with your team to configure and tune FortiSIEM to your security criteria so that it accurately identifies, prioritizes, and alerts on suspicious activity and indicators of compromise.
Our SOC team is well trained to investigate and act on positive alerts. We will work with you to develop custom response playbooks, and train your team on the use of our SOC portal which
provides real-time insights and reporting, so that together, we have an alert handling playbook that matches your business needs. While a SIEM leverages automation, threat intelligence, and machine learning to analyze security data activity and generate alerts, it can only take that analysis so far.
Guided by your custom playbook, PatientLock experts act on threats and either remediate them directly or provide you with actionable advice.
Cyber threats increasingly exploit gaps in a healthcare organization’s security posture created by isolated data pools of security products and the challenges associated with querybased analysis. Query-based analysis requires large amounts of data to be online or restored from backups to search.
PatientLock has a unique method of storing reduplicated behavior attributes associated with each event on a per entity basis. This allows for a historical contextual view over an unlimited time without massive storage requirements. We call it
Persistent Behavior Tracing (PBT).
Find Threats Others Miss, Fill Gaps In Your Security Posture
PBT utilizes a unique hash sum, calculated at processing time, from fields describing each behavior. PBT identifies behaviors via a variety of detection methods determined by the analytics that generate that behavior and each occurrence of a behavior is then tracked using a set of fields specific to that behavior. The result is a system that tracks attack vectors in real time, saves relations indefinitely, and identifies associations based on the threat behavior.
The sophistication of cyber threats continues to evolve. So why do so many cybersecurity tools rely on rule and signaturebased analytics? These tools are good at stopping what they are
programmed to identify, but unfortunately, leave gaps that threat actors find and exploit.
The nLighten XDR platform reviews security data based on more than 250 behaviors. Its machine learning detection recognizes anomalies and finds what others miss to help stay ahead of attackers. We call it Adaptive Analytic Detection (AAD)
Reduce Noisy Alerts 97% More Effectively Than Typical SIEM
nLighten’s machine learning and AI-based behavioral analytic detections analyze massive log and alert volumes to detect behaviors that elude rules and signatures. As a result, AAD recognizes patterns and threats, providing a handful of curated cases instead of thousands of alerts. This gives you an extraordinarily high noise-to-signal ratio, eliminating alert fatigue and improving your security posture with a more accurate, focused approach.
PatientLock’s Cyber Advisor Service consists of a dedicated security professional providing a strategic overlay to your service offerings in effort to enrich your service and advise you on the current state of your cyber program.
As part of this service, your assigned Cyber Advisor will work to understand your unique risk and compliance profile, network environment and business processes. That knowledge combined with
their industry security expertise will be key in helping you assess your current services, interpret reporting metrics, identify potential gaps in your program and provide overall cyber guidance.
Powered By
A Silo-Breaking, Game Changing Solution
Industry-leading extended detection and response utilizes 250+ analytic behavioral detections to give you a fully managed, end-to-end security solution.
Change from reactive to proactive security. Specializing in finding what other products miss, our industry-leading Extended Detection and Response solution leverages a combination of artificial intelligence, machine learning, and behavioral analytics, to proactively identify sophisticated threats before they happen.
Extended Detection and Response (XDR)
For Those About to SOC
Reduce the time to detect and respond to threats in your environment.
Despite your organization’s best efforts, threats can break through your security defenses. And when they do, you need to stop them fast, before they can cause damage.
A security information event management (SIEM) tool is foundational to the visibility and context that fuel effective threat detection and response. A SIEM collects and consolidates security data from devices across your modern distributed environment and normalizes it so that it can be analyzed and monitored for threats.
Managing a SIEM in-house requires staffing, yet an industry talent shortage is underscored by the constantly evolving threats to your business.
Misconfiguration is common and can result in the SIEM generating excessive false alerts, which mask real threats. Not to mention, a SIEM alone can’t tell you how to respond to an alert.
With PatientLock Managed SIEM, you get all the advantages of a SIEM without the complexity.
A SIEM can help you detect and respond to threats in your environment before they can cause damage to your business or patients. PatientLock Managed SIEM offers flexible service levels that can take over wherever your internal team’s bandwidth or skills leave off. Whether you have your own instance of FortiSIEM or use ours, PatientLock skilled analysts and engineers work with your team to configure and tune FortiSIEM to your security criteria so that it accurately identifies, prioritizes, and alerts on suspicious activity and indicators of compromise.
Our SOC team is well trained to investigate and act on positive alerts. We will work with you to develop custom response playbooks, and train your team on the use of our SOC portal which
provides real-time insights and reporting, so that together, we have an alert handling playbook that matches your business needs. While a SIEM leverages automation, threat intelligence, and machine learning to analyze security data activity and generate alerts, it can only take that analysis so far.
Guided by your custom playbook, PatientLock experts act on threats and either remediate them directly or provide you with actionable advice.
Cyber threats increasingly exploit gaps in a healthcare organization’s security posture created by isolated data pools of security products and the challenges associated with querybased analysis. Query-based analysis requires large amounts of data to be online or restored from backups to search.
PatientLock has a unique method of storing reduplicated behavior attributes associated with each event on a per entity basis. This allows for a historical contextual view over an unlimited time without massive storage requirements. We call it
Persistent Behavior Tracing (PBT).
Find Threats Others Miss, Fill Gaps In Your Security Posture
PBT utilizes a unique hash sum, calculated at processing time, from fields describing each behavior. PBT identifies behaviors via a variety of detection methods determined by the analytics that generate that behavior and each occurrence of a behavior is then tracked using a set of fields specific to that behavior. The result is a system that tracks attack vectors in real time, saves relations indefinitely, and identifies associations based on the threat behavior.
The sophistication of cyber threats continues to evolve. So why do so many cybersecurity tools rely on rule and signaturebased analytics? These tools are good at stopping what they are
programmed to identify, but unfortunately, leave gaps that threat actors find and exploit.
The nLighten XDR platform reviews security data based on more than 250 behaviors. Its machine learning detection recognizes anomalies and finds what others miss to help stay ahead of attackers. We call it Adaptive Analytic Detection (AAD)
Reduce Noisy Alerts 97% More Effectively Than Typical SIEM
nLighten’s machine learning and AI-based behavioral analytic detections analyze massive log and alert volumes to detect behaviors that elude rules and signatures. As a result, AAD recognizes patterns and threats, providing a handful of curated cases instead of thousands of alerts. This gives you an extraordinarily high noise-to-signal ratio, eliminating alert fatigue and improving your security posture with a more accurate, focused approach.
PatientLock’s Cyber Advisor Service consists of a dedicated security professional providing a strategic overlay to your service offerings in effort to enrich your service and advise you on the current state of your cyber program.
As part of this service, your assigned Cyber Advisor will work to understand your unique risk and compliance profile, network environment and business processes. That knowledge combined with
their industry security expertise will be key in helping you assess your current services, interpret reporting metrics, identify potential gaps in your program and provide overall cyber guidance.
Powered By
Extended Detection and Response (XDR)
For Those About to SOC
Reduce the time to detect and respond to threats in your environment.
Despite your organization’s best efforts, threats can break through your security defenses. And when they do, you need to stop them fast, before they can cause damage.
A security information event management (SIEM) tool is foundational to the visibility and context that fuel effective threat detection and response. A SIEM collects and consolidates security data from devices across your modern distributed environment and normalizes it so that it can be analyzed and monitored for threats.
Managing a SIEM in-house requires staffing, yet an industry talent shortage is underscored by the constantly evolving threats to your business.
Misconfiguration is common and can result in the SIEM generating excessive false alerts, which mask real threats. Not to mention, a SIEM alone can’t tell you how to respond to an alert.
With PatientLock Managed SIEM, you get all the advantages of a SIEM without the complexity.
A SIEM can help you detect and respond to threats in your environment before they can cause damage to your business or patients. PatientLock Managed SIEM offers flexible service levels that can take over wherever your internal team’s bandwidth or skills leave off. Whether you have your own instance of FortiSIEM or use ours, PatientLock skilled analysts and engineers work with your team to configure and tune FortiSIEM to your security criteria so that it accurately identifies, prioritizes, and alerts on suspicious activity and indicators of compromise.
Our SOC team is well trained to investigate and act on positive alerts. We will work with you to develop custom response playbooks, and train your team on the use of our SOC portal which
provides real-time insights and reporting, so that together, we have an alert handling playbook that matches your business needs. While a SIEM leverages automation, threat intelligence, and machine learning to analyze security data activity and generate alerts, it can only take that analysis so far.
Guided by your custom playbook, PatientLock experts act on threats and either remediate them directly or provide you with actionable advice.
Cyber threats increasingly exploit gaps in a healthcare organization’s security posture created by isolated data pools of security products and the challenges associated with querybased analysis. Query-based analysis requires large amounts of data to be online or restored from backups to search.
PatientLock has a unique method of storing reduplicated behavior attributes associated with each event on a per entity basis. This allows for a historical contextual view over an unlimited time without massive storage requirements. We call it
Persistent Behavior Tracing (PBT).
Find Threats Others Miss, Fill Gaps In Your Security Posture
PBT utilizes a unique hash sum, calculated at processing time, from fields describing each behavior. PBT identifies behaviors via a variety of detection methods determined by the analytics that generate that behavior and each occurrence of a behavior is then tracked using a set of fields specific to that behavior. The result is a system that tracks attack vectors in real time, saves relations indefinitely, and identifies associations based on the threat behavior.
The sophistication of cyber threats continues to evolve. So why do so many cybersecurity tools rely on rule and signaturebased analytics? These tools are good at stopping what they are
programmed to identify, but unfortunately, leave gaps that threat actors find and exploit.
The nLighten XDR platform reviews security data based on more than 250 behaviors. Its machine learning detection recognizes anomalies and finds what others miss to help stay ahead of attackers. We call it Adaptive Analytic Detection (AAD)
Reduce Noisy Alerts 97% More Effectively Than Typical SIEM
nLighten’s machine learning and AI-based behavioral analytic detections analyze massive log and alert volumes to detect behaviors that elude rules and signatures. As a result, AAD recognizes patterns and threats, providing a handful of curated cases instead of thousands of alerts. This gives you an extraordinarily high noise-to-signal ratio, eliminating alert fatigue and improving your security posture with a more accurate, focused approach.
PatientLock’s Cyber Advisor Service consists of a dedicated security professional providing a strategic overlay to your service offerings in effort to enrich your service and advise you on the current state of your cyber program.
As part of this service, your assigned Cyber Advisor will work to understand your unique risk and compliance profile, network environment and business processes. That knowledge combined with
their industry security expertise will be key in helping you assess your current services, interpret reporting metrics, identify potential gaps in your program and provide overall cyber guidance.
Powered By
Managed Detection & Response (MDR)
Managed Detection and Response
Secure your business with simple, affordable enterprise-grade protection
Risk is everywhere in the modern, digitized healthcare environment. Fortunately, PatientLock has you covered, 24/7/365.
In the always-on complex healthcare landscape, businesses face challenges when it comes to implementing a resilient cybersecurity program and achieving compliance against regulatory guidelines.
- Managing multiple, non-integrated security point solutions.
- Lack of Information Technology (IT) and Information Security (IS) resources.
- Historic costs of security technology and services.
- Competing priorities like patient care, maintaining EMR and PM systems, etc.
Using our technology and people, PatientLock Managed Detection and Response (MDR) eliminates barriers to better security.
We protect your business 24/7/365
On-premise legacy systems
Networks
Perimeter Devices (i.e. firewall, UTM)
Active Directory
DNS
Intrusion Detection & Prevention Systems
Cloud Applications
Cloud Storage
Protect
Our team of specialized security experts is laser focused on protecting your organization and assets 24/7/365, so you can focus on patients.
Detect
Powerful and integrated technologies, machine learning, and enterprise-grade threat intelligence help PatientLock analysts identify malicious activity faster than any other security solution on the market.
Respond
Once a critical threat is identified, PatientLock contains it and closes the gap to mitigate future exploitation.
Powered By
Secure Your Business with Simple, Affordable Enterprise-grade Protection
Clinical information systems (EMRs) and the widespread use of email and telehealth platforms has created massive attack surface. Risk is everywhere in the modern healthcare environment, so it’s critical that you protect your business and patients. Unfortunately, common cybersecurity challenges faced by healthcare organizations can be barriers to your success.
PatientLock Managed Detection and Response (MDR) eliminates barriers to better information security. Designed to force-multiply existing IT or IS resources, PatientLock’s managed-services model makes protecting modern healthcare environments possible, delivering effective cybersecurity protection designed to fit any healthcare business, or budget.
Managed Detection and Response
Secure your business with simple, affordable enterprise-grade protection
Risk is everywhere in the modern, digitized healthcare environment. Fortunately, PatientLock has you covered, 24/7/365.
In the always-on complex healthcare landscape, businesses face challenges when it comes to implementing a resilient cybersecurity program and achieving compliance against regulatory guidelines.
- Managing multiple, non-integrated security point solutions.
- Lack of Information Technology (IT) and Information Security (IS) resources.
- Historic costs of security technology and services.
- Competing priorities like patient care, maintaining EMR and PM systems, etc.
Using our technology and people, PatientLock Managed Detection and Response (MDR) eliminates barriers to better security.
We protect your business 24/7/365
On-premise legacy systems
Networks
Perimeter Devices (i.e. firewall, UTM)
Active Directory
DNS
Intrusion Detection & Prevention Systems
Cloud Applications
Cloud Storage
Protect
Our team of specialized security experts is laser focused on protecting your organization and assets 24/7/365, so you can focus on patients.
Detect
Powerful and integrated technologies, machine learning, and enterprise-grade threat intelligence help PatientLock analysts identify malicious activity faster than any other security solution on the market.
Respond
Once a critical threat is identified, PatientLock contains it and closes the gap to mitigate future exploitation.
Powered By
Managed Detection and Response
Secure your business with simple, affordable enterprise-grade protection
Risk is everywhere in the modern, digitized healthcare environment. Fortunately, PatientLock has you covered, 24/7/365.
In the always-on complex healthcare landscape, businesses face challenges when it comes to implementing a resilient cybersecurity program and achieving compliance against regulatory guidelines.
- Managing multiple, non-integrated security point solutions.
- Lack of Information Technology (IT) and Information Security (IS) resources.
- Historic costs of security technology and services.
- Competing priorities like patient care, maintaining EMR and PM systems, etc.
Using our technology and people, PatientLock Managed Detection and Response (MDR) eliminates barriers to better security.
We protect your business 24/7/365
On-premise legacy systems
Networks
Perimeter Devices (i.e. firewall, UTM)
Active Directory
DNS
Intrusion Detection & Prevention Systems
Cloud Applications
Cloud Storage
Protect
Our team of specialized security experts is laser focused on protecting your organization and assets 24/7/365, so you can focus on patients.
Detect
Powerful and integrated technologies, machine learning, and enterprise-grade threat intelligence help PatientLock analysts identify malicious activity faster than any other security solution on the market.
Respond
Once a critical threat is identified, PatientLock contains it and closes the gap to mitigate future exploitation.
Powered By
Managed Endpoint Detection & Response (EDR)
Managed Endpoint Detection and Response
PatientLock Managed Endpoint Detection and Response (Managed EDR) delivers unparalleled visibility into your endpoint ecosystem. SentinelOne's AI-powered agents are the first line-of-defense, hunting for threats and blocking things like malware and ransomware at the endpoints, while PatientLock's skilled analysts monitor the environment remotely for signs of compromise. These real-time defenses work together to detect and remediate threats — before they can impact your business, or your patients.
The best part? We're doing the work and managing the technology behind-the-scenes so you can focus on patient care.
Protection at Your Endpoints
Stop file-less attacks
Block malware and trojans
Contain activity at machine speed
Policy-based controls
Maps to known vulnerabilities
Remote shell for responder access
Autonomous threat hunting, capture, quarantine, as well as device roll-back.
Detects and Remediates Endpoint Threats
PatientLock Managed EDR delivers complete visibility of the endpoint devices in your business and clinical environments. Single-purpose, artificial intelligence powered agents monitor device, data, and application activity - working with or without cloud connectivity to automatically detect file-less attacks (memory exploits, script misuse, etc.) and block malware and ransomware directly at the endpoint.
Our experienced cybersecurity analysts add the human component and critical value by monitoring this activity remotely in real-time.
Automated policy-based controls manage network connectivity to and from assets and USB peripheral devices; mapping to the MITRE CVE database provides insight into known vulnerabilities. As a managed service, PatientLock Managed EDR does the heavy lifting to detect and remediate endpoint threats, removing the burden of endpoint protection from internal teams.
Real-time
Complete and real-time visibility and context into activity at your endpoints reduces time between endpoint compromise and detection.
Unified
Single, purpose-built endpoint agents and remote endpoint monitoring by our experienced security team deliver holistic, active protection.
Contextual
Automation strings together key EDR incidents for the critical context our analysts need to quickly assess and contain potential incidents.
Powered By
Featuring SentinelOne’s Singularity Complete
From laptops and desktops to servers and mobile devices, endpoints expose healthcare organizations to sophisticated threats. Organizations have their work cut out for them, balancing an escalating number of endpoints with effective threat protection across the digital environment. Endpoints are a major entry point for disruptive threats. Legacy anti-virus and endpoint protection programs simply aren’t responsive enough to stop modern attacks.
By layering 24/7/365 managed detection and response (MDR) over SentinelOne’s Singularity Complete, PatientLock makes it simple to defend against endpoint risk.
Managed Endpoint Detection and Response
PatientLock Managed Endpoint Detection and Response (Managed EDR) delivers unparalleled visibility into your endpoint ecosystem. SentinelOne's AI-powered agents are the first line-of-defense, hunting for threats and blocking things like malware and ransomware at the endpoints, while PatientLock's skilled analysts monitor the environment remotely for signs of compromise. These real-time defenses work together to detect and remediate threats — before they can impact your business, or your patients.
The best part? We're doing the work and managing the technology behind-the-scenes so you can focus on patient care.

Protection at Your Endpoints
Stop file-less attacks
Block malware and trojans
Contain activity at machine speed
Policy-based controls
Maps to known vulnerabilities
Remote shell for responder access
Autonomous threat hunting, capture, quarantine, as well as device roll-back.
Detects and Remediates Endpoint Threats
PatientLock Managed EDR delivers complete visibility of the endpoint devices in your business and clinical environments. Single-purpose, artificial intelligence powered agents monitor device, data, and application activity - working with or without cloud connectivity to automatically detect file-less attacks (memory exploits, script misuse, etc.) and block malware and ransomware directly at the endpoint.
Our experienced cybersecurity analysts add the human component and critical value by monitoring this activity remotely in real-time.
Automated policy-based controls manage network connectivity to and from assets and USB peripheral devices; mapping to the MITRE CVE database provides insight into known vulnerabilities. As a managed service, PatientLock Managed EDR does the heavy lifting to detect and remediate endpoint threats, removing the burden of endpoint protection from internal teams.
Real-time
Complete and real-time visibility and context into activity at your endpoints reduces time between endpoint compromise and detection.
Unified
Single, purpose-built endpoint agents and remote endpoint monitoring by our experienced security team deliver holistic, active protection.
Contextual
Automation strings together key EDR incidents for the critical context our analysts need to quickly assess and contain potential incidents.
Powered By
Managed Endpoint Detection and Response
PatientLock Managed Endpoint Detection and Response (Managed EDR) delivers unparalleled visibility into your endpoint ecosystem. SentinelOne's AI-powered agents are the first line-of-defense, hunting for threats and blocking things like malware and ransomware at the endpoints, while PatientLock's skilled analysts monitor the environment remotely for signs of compromise. These real-time defenses work together to detect and remediate threats — before they can impact your business, or your patients.
The best part? We're doing the work and managing the technology behind-the-scenes so you can focus on patient care.

Protection at Your Endpoints
Stop file-less attacks
Block malware and trojans
Contain activity at machine speed
Policy-based controls
Maps to known vulnerabilities
Remote shell for responder access
Autonomous threat hunting, capture, quarantine, as well as device roll-back.
Detects and Remediates Endpoint Threats
PatientLock Managed EDR delivers complete visibility of the endpoint devices in your business and clinical environments. Single-purpose, artificial intelligence powered agents monitor device, data, and application activity - working with or without cloud connectivity to automatically detect file-less attacks (memory exploits, script misuse, etc.) and block malware and ransomware directly at the endpoint.
Our experienced cybersecurity analysts add the human component and critical value by monitoring this activity remotely in real-time.
Automated policy-based controls manage network connectivity to and from assets and USB peripheral devices; mapping to the MITRE CVE database provides insight into known vulnerabilities. As a managed service, PatientLock Managed EDR does the heavy lifting to detect and remediate endpoint threats, removing the burden of endpoint protection from internal teams.
Real-time
Complete and real-time visibility and context into activity at your endpoints reduces time between endpoint compromise and detection.
Unified
Single, purpose-built endpoint agents and remote endpoint monitoring by our experienced security team deliver holistic, active protection.
Contextual
Automation strings together key EDR incidents for the critical context our analysts need to quickly assess and contain potential incidents.
Powered By
Email Protection Services
Email Protection Services
Proactive Protection for Your Most Vulnerable System
Email is core to business and patient communication – and healthcare's number one attack vector. PatientLock makes email secure, and compliant.
From sophisticated payloads like malware and ransomware to social engineering tactics preying on human endpoints, email attacks can flatline a healthcare organization. Email operations must be secure against both external attacks and insider threats, while complying with stringent and evolving regulations designed to protect ePHI as well as corporate data – at rest, and in transit.
Real-Time Defense Against:
Spam, Malware, and Viruses
Social Engineering (phishing, baiting, etc.)
Imposter Threats
Business Email Compromise Scams
Exfiltration
Negligance and Human Error
Wire and Vendor Fraud
Insider Threats
A Simple Solution to a Complex Threat
PatientLock EPS delivers secure and multi-layered defense using Artificial Intelligence and Machine Learning for protection against social engineering attempts, as well as encryption and data loss prevention (DLP). Behind the technology, PatientLock EPS is backed by 24x7x365 security operations center monitoring, where top-tier security analysts prioritize and handle threats against email systems.
The result?
Powerful, Advanced Protection Against Modern Threats
PatientLock EPS integrates with Google, Office 365, and other services both on-prem and in the cloud. Secure, offsite archiving ensures business continuity and provides easy access for e-discovery and audit requests, while patient data and business communications remain secure and compliant without the burden or cost of additional staffing, implementing, or maintaining an in-house email security solution.
Advanced Defense
More than just signature-based protection, enterprise-grade artificial intelligence and machine learning tools analyze email attributes and user behavior to predict and detect evasive threats.
Content-Aware Policies
Data Loss Prevention (DLP) guards against the loss of intellectual property, customer, and corporate data with policies that work against external/internal threats and accidental loss.
Robust Compliance
Compliance policy packs make it easy to comply with email related policies set by federal regulations like HIPAA, as well as cybersecurity frameworks like NIST CSF and PCI-DSS.
Proactive Protection for Healthcare’s Most Vulnerable System
Email is now a core tool used for business and patient communication. It’s also the number one attack vector.
PatientLock Email Protection Services (EPS) provides 24/7/365 proactive protection for your most critical – and most vulnerable system.
PatientLock Email Protection Services (EPS) makes it simple to defend against email threats, ensure business continuity, and satisfy compliance and audit obligations. Whether you need protection for your existing, on-prem, cloud-based, or hybrid email solution, PatientLock simplifies email protection.
Email Protection Services
Proactive Protection for Your Most Vulnerable System
Email is core to business and patient communication – and healthcare's number one attack vector. PatientLock makes email secure, and compliant.
From sophisticated payloads like malware and ransomware to social engineering tactics preying on human endpoints, email attacks can flatline a healthcare organization. Email operations must be secure against both external attacks and insider threats, while complying with stringent and evolving regulations designed to protect ePHI as well as corporate data – at rest, and in transit.

Real-Time Defense Against:
Spam, Malware, and Viruses
Social Engineering (phishing, baiting, etc.)
Imposter Threats
Business Email Compromise Scams
Exfiltration
Negligance and Human Error
Wire and Vendor Fraud
Insider Threats
A Simple Solution to a Complex Threat
PatientLock EPS delivers secure and multi-layered defense using Artificial Intelligence and Machine Learning for protection against social engineering attempts, as well as encryption and data loss prevention (DLP). Behind the technology, PatientLock EPS is backed by 24x7x365 security operations center monitoring, where top-tier security analysts prioritize and handle threats against email systems.
The result?
Powerful, Advanced Protection Against Modern Threats
PatientLock EPS integrates with Google, Office 365, and other services both on-prem and in the cloud. Secure, offsite archiving ensures business continuity and provides easy access for e-discovery and audit requests, while patient data and business communications remain secure and compliant without the burden or cost of additional staffing, implementing, or maintaining an in-house email security solution.
Advanced Defense
More than just signature-based protection, enterprise-grade artificial intelligence and machine learning tools analyze email attributes and user behavior to predict and detect evasive threats.
Content-Aware Policies
Data Loss Prevention (DLP) guards against the loss of intellectual property, customer, and corporate data with policies that work against external/internal threats and accidental loss.
Robust Compliance
Compliance policy packs make it easy to comply with email related policies set by federal regulations like HIPAA, as well as cybersecurity frameworks like NIST CSF and PCI-DSS.
Email Protection Services
Proactive Protection for Your Most Vulnerable System
Email is core to business and patient communication – and healthcare's number one attack vector. PatientLock makes email secure, and compliant.
From sophisticated payloads like malware and ransomware to social engineering tactics preying on human endpoints, email attacks can flatline a healthcare organization. Email operations must be secure against both external attacks and insider threats, while complying with stringent and evolving regulations designed to protect ePHI as well as corporate data – at rest, and in transit.

Real-Time Defense Against:
Spam, Malware, and Viruses
Social Engineering (phishing, baiting, etc.)
Imposter Threats
Business Email Compromise Scams
Exfiltration
Negligance and Human Error
Wire and Vendor Fraud
Insider Threats
A Simple Solution to a Complex Threat
PatientLock EPS delivers secure and multi-layered defense using Artificial Intelligence and Machine Learning for protection against social engineering attempts, as well as encryption and data loss prevention (DLP). Behind the technology, PatientLock EPS is backed by 24x7x365 security operations center monitoring, where top-tier security analysts prioritize and handle threats against email systems.
The result?
Powerful, Advanced Protection Against Modern Threats
PatientLock EPS integrates with Google, Office 365, and other services both on-prem and in the cloud. Secure, offsite archiving ensures business continuity and provides easy access for e-discovery and audit requests, while patient data and business communications remain secure and compliant without the burden or cost of additional staffing, implementing, or maintaining an in-house email security solution.
Advanced Defense
More than just signature-based protection, enterprise-grade artificial intelligence and machine learning tools analyze email attributes and user behavior to predict and detect evasive threats.
Content-Aware Policies
Data Loss Prevention (DLP) guards against the loss of intellectual property, customer, and corporate data with policies that work against external/internal threats and accidental loss.
Robust Compliance
Compliance policy packs make it easy to comply with email related policies set by federal regulations like HIPAA, as well as cybersecurity frameworks like NIST CSF and PCI-DSS.
Multi-Factor Authentication (MFA)
Multi-factor Authentication
Scalable Access Security That’s Simple and Powerful
Get secure access for any user and device to any environment, from anywhere.
The shift to hybrid work models and perimeter-less environments amplifies the need for security to shift too. Today, your data and applications no longer sit behind a corporate firewall – and neither do your users.
You need assurance that only the right users and secure devices are accessing your applications and systems every time.
The use of strong authentication increases your security, but not all solutions are the same. Cost, flexibility, and the complexity of deployment and use can vary across solutions.
Trusted Access
MFA means users provide a password plus a second source of validation (e.g., authorization code) to verify their identity before access is granted.
Fast Deployment
Add MFA to any existing environment or platform – fast. Our self-enrollment feature makes it easy for users to get set up.
User-friendly
Intuitive with fast set up and multiple authentication options to choose from, PatientLock's MFA solutions keep users secure without being disruptive.
Scalable
Easily set up new users, support new devices, and protect new applications without impacting existing technology.
PatientLock MFA
A Win-Win for Your Users and Your Security Team
It’s time to go beyond basic protection – and PatientLock MFA is a smart step. Don’t let your users hold the door open for an attacker by requiring only a username and password to validate user identity.
PatientLock MFA gives you peace-of-mind with strong, trusted access protection across any business or clinical environment, and allows users to access applications securely, and quickly. With multiple authentication options, users can choose the method that’s most convenient for them, without disrupting their productivity or slowing down patient throughput.
As with all of our services, PatientLock makes access to strong MFA affordable and simple – and scales easily to accommodate new users, devices, applications, and environments. Our flexible, cloud-based solution is easy to deploy and operate and allows your team to set rules-based policies for different users, devices, and applications as well as activate MFA for assets as needed and on-the-fly.
Powered By

Scalable Access Security That’s Simple and Powerful
Get secure access for any user and device to any environment, from anywhere.
The shift to hybrid work models and perimeterless environments amplifies the need for security to shift too. Today, your data and applications no longer sit behind a corporate firewall – and neither do your users.
You need assurance that only the right users and secure devices are accessing your applications and systems every time.
The use of strong authentication increases your security, but not all solutions are the same. Cost, flexibility, and the complexity of deployment and use can vary across solutions.
Multi-factor Authentication
Scalable Access Security That’s Simple and Powerful
Get secure access for any user and device to any environment, from anywhere.
The shift to hybrid work models and perimeter-less environments amplifies the need for security to shift too. Today, your data and applications no longer sit behind a corporate firewall – and neither do your users.
You need assurance that only the right users and secure devices are accessing your applications and systems every time.
The use of strong authentication increases your security, but not all solutions are the same. Cost, flexibility, and the complexity of deployment and use can vary across solutions.
Trusted Access
MFA means users provide a password plus a second source of validation (e.g., authorization code) to verify their identity before access is granted.
Fast Deployment
Add MFA to any existing environment or platform – fast. Our self-enrollment feature makes it easy for users to get set up.
User-friendly
Intuitive with fast set up and multiple authentication options to choose from, PatientLock's MFA solutions keep users secure without being disruptive.
Scalable
Easily set up new users, support new devices, and protect new applications without impacting existing technology.
PatientLock MFA
A Win-Win for Your Users and Your Security Team
It’s time to go beyond basic protection – and PatientLock MFA is a smart step. Don’t let your users hold the door open for an attacker by requiring only a username and password to validate user identity.
PatientLock MFA gives you peace-of-mind with strong, trusted access protection across any business or clinical environment, and allows users to access applications securely, and quickly. With multiple authentication options, users can choose the method that’s most convenient for them, without disrupting their productivity or slowing down patient throughput.
As with all of our services, PatientLock makes access to strong MFA affordable and simple – and scales easily to accommodate new users, devices, applications, and environments. Our flexible, cloud-based solution is easy to deploy and operate and allows your team to set rules-based policies for different users, devices, and applications as well as activate MFA for assets as needed and on-the-fly.
Powered By

Multi-factor Authentication
Scalable Access Security That’s Simple and Powerful
Get secure access for any user and device to any environment, from anywhere.
The shift to hybrid work models and perimeter-less environments amplifies the need for security to shift too. Today, your data and applications no longer sit behind a corporate firewall – and neither do your users.
You need assurance that only the right users and secure devices are accessing your applications and systems every time.
The use of strong authentication increases your security, but not all solutions are the same. Cost, flexibility, and the complexity of deployment and use can vary across solutions.
Trusted Access
MFA means users provide a password plus a second source of validation (e.g., authorization code) to verify their identity before access is granted.
Fast Deployment
Add MFA to any existing environment or platform – fast. Our self-enrollment feature makes it easy for users to get set up.
User-friendly
Intuitive with fast set up and multiple authentication options to choose from, PatientLock's MFA solutions keep users secure without being disruptive.
Scalable
Easily set up new users, support new devices, and protect new applications without impacting existing technology.
PatientLock MFA
A Win-Win for Your Users and Your Security Team
It’s time to go beyond basic protection – and PatientLock MFA is a smart step. Don’t let your users hold the door open for an attacker by requiring only a username and password to validate user identity.
PatientLock MFA gives you peace-of-mind with strong, trusted access protection across any business or clinical environment, and allows users to access applications securely, and quickly. With multiple authentication options, users can choose the method that’s most convenient for them, without disrupting their productivity or slowing down patient throughput.
As with all of our services, PatientLock makes access to strong MFA affordable and simple – and scales easily to accommodate new users, devices, applications, and environments. Our flexible, cloud-based solution is easy to deploy and operate and allows your team to set rules-based policies for different users, devices, and applications as well as activate MFA for assets as needed and on-the-fly.
Powered By

Managed Firewall
Managed Firewall
Next-gen network defense made simple and affordable
Digital initiatives, tele-health, remote work, and distributed office locations are testing the bounds of traditional perimeter-based security.
While the data center still exists, it is no longer the nucleus of the healthcare organization’s IT operations. Systems, applications, and protected health information can reside anywhere – from the ground to the cloud, to third-party services – and in distributed and hybrid networks. Users and clinicians now access these assets from multiple locations and multiple devices.
As a healthcare organization extends its reach into new environments, it also extends its attack surface. Consistent
protection is critical along the network edge.
PatientLock's Managed Firewall adds critical functionality that strengthens a healthcare organization's defense of its users, patients, and digital assets in a modern, perimeter-less world.
Features
Inspects web services messages including SOAP and XML, both document- and PRC-oriented models
Inspects web page content, such as HTML, Dynamic HTML, and CSS, along with the underlying protocols such as HTTP and HTTPS
Helps meet HIPAA HITECH sections 164.308(a)(5)(i) and 164.312(c)(1)
Covers PCI DSS 2.0 requirements 6.5, 6.6, OWASP top ten, 10.5.4, & configuration change process
Monitors both clear text and SSL encrypted traffic
Supports both whitelist and blacklist source IP address security models
Protect valuable web-based resources
Protects multiple web application servers simultaneously
Supports customer-specific rule sets
Includes automatic rule updates
Multiple deployment options:
In-line and out-of-band: the Web Application Firewall acts as a reverse proxy for the application traffic
Virtual deployment: the Web Application Firewall can be in multiple virtual environments
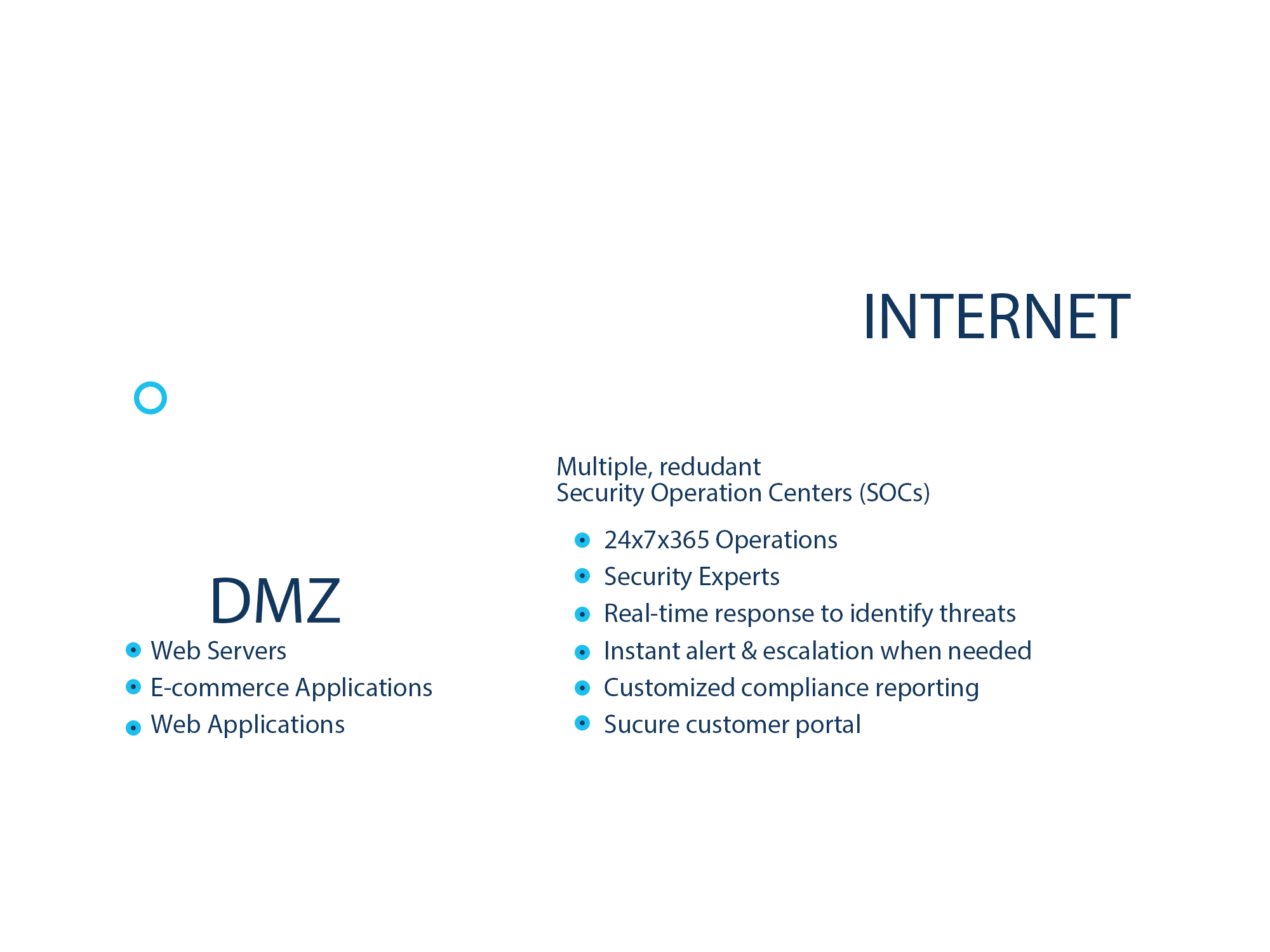
The Trusted Security Experts
We’ll call, text, or email you during business hours, or 24x7, your choice. If you need help with your service, a change to your configuration, or just havea question, our amazing 3-ring service gets you quickly to an expert analyst 24x7.
When you’re ready to expand, you can add as many security appliances as you like, and PatientLock offers a variety of other security and compliance services to increase your level of protection, and help you become compliant with PCI or HIPAA requirements and regulations.
Powered By

Reveal Hidden threats with PatientLock
The PatientLock Web Application Firewall (WAF) service protects your web-based applications from attack by monitoring input, output and access attempts, and blocking any malicious activity.
When attacks are detected, the Web Application Firewall alerts analysts in our Security Operations Centers (SOCs) and immediately blocks the originating IP address. The service protects against the full range of application vulnerabilities including cross-site scripting (XSS), injection flaws (SQL, LDAP, Xpath and others), malicious file execution, insecure direct object references, cross-site request forgery (CSRF), information leakage and improper error handling, broken authentications and session management, insecure cryptographic storage, insecure communications, and failure to restrict URL access threats more quickly.
Managed Firewall
Next-gen network defense made simple and affordable
Digital initiatives, tele-health, remote work, and distributed office locations are testing the bounds of traditional perimeter-based security.
While the data center still exists, it is no longer the nucleus of the healthcare organization’s IT operations. Systems, applications, and protected health information can reside anywhere – from the ground to the cloud, to third-party services – and in distributed and hybrid networks. Users and clinicians now access these assets from multiple locations and multiple devices.
As a healthcare organization extends its reach into new environments, it also extends its attack surface. Consistent
protection is critical along the network edge.
PatientLock's Managed Firewall adds critical functionality that strengthens a healthcare organization's defense of its users, patients, and digital assets in a modern, perimeter-less world.
Features
Inspects web services messages including SOAP and XML, both document- and PRC-oriented models
Inspects web page content, such as HTML, Dynamic HTML, and CSS, along with the underlying protocols such as HTTP and HTTPS
Helps meet HIPAA HITECH sections 164.308(a)(5)(i) and 164.312(c)(1)
Covers PCI DSS 2.0 requirements 6.5, 6.6, OWASP top ten, 10.5.4, & configuration change process
Monitors both clear text and SSL encrypted traffic
Supports both whitelist and blacklist source IP address security models
Protect valuable web-based resources
Protects multiple web application servers simultaneously
Supports customer-specific rule sets
Includes automatic rule updates
Multiple deployment options:
In-line and out-of-band: the Web Application Firewall acts as a reverse proxy for the application traffic
Virtual deployment: the Web Application Firewall can be in multiple virtual environments

The Trusted Security Experts
We’ll call, text, or email you during business hours, or 24x7, your choice. If you need help with your service, a change to your configuration, or just havea question, our amazing 3-ring service gets you quickly to an expert analyst 24x7.
When you’re ready to expand, you can add as many security appliances as you like, and PatientLock offers a variety of other security and compliance services to increase your level of protection, and help you become compliant with PCI or HIPAA requirements and regulations.
Powered By

Managed Firewall
Next-gen network defense made simple and affordable
Digital initiatives, tele-health, remote work, and distributed office locations are testing the bounds of traditional perimeter-based security.
While the data center still exists, it is no longer the nucleus of the healthcare organization’s IT operations. Systems, applications, and protected health information can reside anywhere – from the ground to the cloud, to third-party services – and in distributed and hybrid networks. Users and clinicians now access these assets from multiple locations and multiple devices.
As a healthcare organization extends its reach into new environments, it also extends its attack surface. Consistent
protection is critical along the network edge.
PatientLock's Managed Firewall adds critical functionality that strengthens a healthcare organization's defense of its users, patients, and digital assets in a modern, perimeter-less world.
Features
Inspects web services messages including SOAP and XML, both document- and PRC-oriented models
Inspects web page content, such as HTML, Dynamic HTML, and CSS, along with the underlying protocols such as HTTP and HTTPS
Helps meet HIPAA HITECH sections 164.308(a)(5)(i) and 164.312(c)(1)
Covers PCI DSS 2.0 requirements 6.5, 6.6, OWASP top ten, 10.5.4, & configuration change process
Monitors both clear text and SSL encrypted traffic
Supports both whitelist and blacklist source IP address security models
Protect valuable web-based resources
Protects multiple web application servers simultaneously
Supports customer-specific rule sets
Includes automatic rule updates
Multiple deployment options:
In-line and out-of-band: the Web Application Firewall acts as a reverse proxy for the application traffic
Virtual deployment: the Web Application Firewall can be in multiple virtual environments

The Trusted Security Experts
We’ll call, text, or email you during business hours, or 24x7, your choice. If you need help with your service, a change to your configuration, or just havea question, our amazing 3-ring service gets you quickly to an expert analyst 24x7.
When you’re ready to expand, you can add as many security appliances as you like, and PatientLock offers a variety of other security and compliance services to increase your level of protection, and help you become compliant with PCI or HIPAA requirements and regulations.
Powered By

Vulnerability Management
Vulnerability Management
Close the gaps that expose your business to risks
Unmanaged vulnerabilities pose critical risk to your healthcare business. PatientLock helps you detect, prioritize, and remediate vulnerabilities, effectively.
IT-resources in healthcare managing the critical systems required to see patients are stretched thin, which means vulnerability management can be tough to keep up on.
Here's why: Not all vulnerabilities pose risk to your business, but in order to know which ones do, you’ll need to identify and prioritize the business critical systems and software in your environment. Remediation efforts, including software patches and configuration changes must be identified, tested, and deployed. To be effective, all of these efforts need to be done monthly, which can easily overwhelm
already stretched internal resources.
PatientLock Vulnerability Management takes the complexity out of detecting, prioritizing, and remediating issues in your environment. We deliver the skilled resources, processes, and technology needed to manage the full vulnerability life cycle – helping you find and fix
potential exposures before they can be exploited. With PatientLock, continuous risk-based vulnerability management is achievable – with
less burden on your already-stretched internal team.
Full Life-Cycle Management
- Proactive Vulnerability Scanning
- Risk Based Prioritization of Gaps
- Guided Remediation
- Validation Scans
- Compliance Support
- Auditable Change Management
- Automated Reporting
PatientLock Vulnerability Management
Real-Time Visibility, Continuous Risk Management
PatientLock Vulnerability Management delivers unparalleled, continuous visibility into vulnerabilities in your environment that can expose your organization and patients to risk. These include un-patched software, software coding issues, and improper system configurations.
A managed service provider, PatientLock takes the complexity out of full life-cycle vulnerability management, from the discovery of business critical assets to issue detection, risk-based remediation and validation, to reporting.
Our integrated platform combines leading technologies, automated tools, and the latest threat intelligence to allow our analysts to spot potential exposures and weaknesses. We use a risk-based approach to prioritize Identified issues based on the degree of risk they pose to your business. Our experts guide you through issue remediation, which can include configuration changes and patches, as well as validation scans to verify remediation success, with reports to demonstrate the risk management process for auditors and executives.
Powered By

Continuous Attack-Surface Management
A lot of companies scan for vulnerabilities yet scans alone don’t reduce risk. They simply identify vulnerabilities – often in large numbers. Not all vulnerabilities pose risk to your business, either. Those that have been weaponized and are exploitable do.
PatientLock Vulnerability Management takes the complexity out of detecting, prioritizing, and remediating vulnerabilities in your environment by delivering the skilled resources, processes, and technology needed to continuously manage your attack surface and vulnerability life cycle – helping you find and fix potential exposures before they can be exploited.
Vulnerability Management
Close the gaps that expose your business to risks
Unmanaged vulnerabilities pose critical risk to your healthcare business. PatientLock helps you detect, prioritize, and remediate vulnerabilities, effectively.
IT-resources in healthcare managing the critical systems required to see patients are stretched thin, which means vulnerability management can be tough to keep up on.
Here's why: Not all vulnerabilities pose risk to your business, but in order to know which ones do, you’ll need to identify and prioritize the business critical systems and software in your environment. Remediation efforts, including software patches and configuration changes must be identified, tested, and deployed. To be effective, all of these efforts need to be done monthly, which can easily overwhelm
already stretched internal resources.
PatientLock Vulnerability Management takes the complexity out of detecting, prioritizing, and remediating issues in your environment. We deliver the skilled resources, processes, and technology needed to manage the full vulnerability life cycle – helping you find and fix
potential exposures before they can be exploited. With PatientLock, continuous risk-based vulnerability management is achievable – with
less burden on your already-stretched internal team.
Full Life-Cycle Management
- Proactive Vulnerability Scanning
- Risk Based Prioritization of Gaps
- Guided Remediation
- Validation Scans
- Compliance Support
- Auditable Change Management
- Automated Reporting

PatientLock Vulnerability Management
Real-Time Visibility, Continuous Risk Management
PatientLock Vulnerability Management delivers unparalleled, continuous visibility into vulnerabilities in your environment that can expose your organization and patients to risk. These include un-patched software, software coding issues, and improper system configurations.
A managed service provider, PatientLock takes the complexity out of full life-cycle vulnerability management, from the discovery of business critical assets to issue detection, risk-based remediation and validation, to reporting.
Our integrated platform combines leading technologies, automated tools, and the latest threat intelligence to allow our analysts to spot potential exposures and weaknesses. We use a risk-based approach to prioritize Identified issues based on the degree of risk they pose to your business. Our experts guide you through issue remediation, which can include configuration changes and patches, as well as validation scans to verify remediation success, with reports to demonstrate the risk management process for auditors and executives.
Powered By

Vulnerability Management
Close the gaps that expose your business to risks
Unmanaged vulnerabilities pose critical risk to your healthcare business. PatientLock helps you detect, prioritize, and remediate vulnerabilities, effectively.
IT-resources in healthcare managing the critical systems required to see patients are stretched thin, which means vulnerability management can be tough to keep up on.
Here's why: Not all vulnerabilities pose risk to your business, but in order to know which ones do, you’ll need to identify and prioritize the business critical systems and software in your environment. Remediation efforts, including software patches and configuration changes must be identified, tested, and deployed. To be effective, all of these efforts need to be done monthly, which can easily overwhelm
already stretched internal resources.
PatientLock Vulnerability Management takes the complexity out of detecting, prioritizing, and remediating issues in your environment. We deliver the skilled resources, processes, and technology needed to manage the full vulnerability life cycle – helping you find and fix
potential exposures before they can be exploited. With PatientLock, continuous risk-based vulnerability management is achievable – with
less burden on your already-stretched internal team.
Full Life-Cycle Management
- Proactive Vulnerability Scanning
- Risk Based Prioritization of Gaps
- Guided Remediation
- Validation Scans
- Compliance Support
- Auditable Change Management
- Automated Reporting

PatientLock Vulnerability Management
Real-Time Visibility, Continuous Risk Management
PatientLock Vulnerability Management delivers unparalleled, continuous visibility into vulnerabilities in your environment that can expose your organization and patients to risk. These include un-patched software, software coding issues, and improper system configurations.
A managed service provider, PatientLock takes the complexity out of full life-cycle vulnerability management, from the discovery of business critical assets to issue detection, risk-based remediation and validation, to reporting.
Our integrated platform combines leading technologies, automated tools, and the latest threat intelligence to allow our analysts to spot potential exposures and weaknesses. We use a risk-based approach to prioritize Identified issues based on the degree of risk they pose to your business. Our experts guide you through issue remediation, which can include configuration changes and patches, as well as validation scans to verify remediation success, with reports to demonstrate the risk management process for auditors and executives.
Powered By

IoMT Security
IoMT Security with Medigate
A Modular, SaaS-powered healthcare IoMT Security platform that scales to protect your environment, address your use cases, and fulfill your goals as they evolve
Powered By

Extends cybersecurity across your healthcare XIoT
A broad range of XIoT devices ensure care delivery in your healthcare environment: from IV pumps and ultrasounds, to smart HVAC and lighting systems. Medigate secures them all.
Supports your full healthcare cybersecurity journey
Whether you want to automate asset discovery, combat zero-day attacks, or aren’t sure where to start, Medigate will support and grow with you on your entire journey.
Designed for scalability, flexibility, and ease-of-use
As a SaaS solution with a flexible UI built to adapt to all IT, security, Biomed, and executive needs, Medigate deploys and scales effortlessly no matter the user or use case.
Integrates seamlessly with your existing tech stack
Medigate's extensive technical ecosystem integrations empower you to easily extend your existing security infrastructure to your healthcare environment.
Protecting Connected Medical Devices with Medigate
Unlike connected devices in traditional Internet of Things (IoT) deployments, attacks on devices in the Internet of Medical Things (IoMT) can have fatal consequences for patients, as well as devastating implications for healthcare providers’ reputations. Protecting connected medical devices poses several unique challenges that traditional IoT security solutions cannot address.
IoMT Security with Medigate
A Modular, SaaS-powered healthcare IoMT Security platform that scales to protect your environment, address your use cases, and fulfill your goals as they evolve
Powered By

Extends cybersecurity across your healthcare XIoT
A broad range of XIoT devices ensure care delivery in your healthcare environment: from IV pumps and ultrasounds, to smart HVAC and lighting systems. Medigate secures them all.
Supports your full healthcare cybersecurity journey
Whether you want to automate asset discovery, combat zero-day attacks, or aren’t sure where to start, Medigate will support and grow with you on your entire journey.
Designed for scalability, flexibility, and ease-of-use
As a SaaS solution with a flexible UI built to adapt to all IT, security, Biomed, and executive needs, Medigate deploys and scales effortlessly no matter the user or use case.
Integrates seamlessly with your existing tech stack
Medigate's extensive technical ecosystem integrations empower you to easily extend your existing security infrastructure to your healthcare environment.
IoMT Security with Medigate
A Modular, SaaS-powered healthcare IoMT Security platform that scales to protect your environment, address your use cases, and fulfill your goals as they evolve
Powered By

Extends cybersecurity across your healthcare XIoT
A broad range of XIoT devices ensure care delivery in your healthcare environment: from IV pumps and ultrasounds, to smart HVAC and lighting systems. Medigate secures them all.
Supports your full healthcare cybersecurity journey
Whether you want to automate asset discovery, combat zero-day attacks, or aren’t sure where to start, Medigate will support and grow with you on your entire journey.
Designed for scalability, flexibility, and ease-of-use
As a SaaS solution with a flexible UI built to adapt to all IT, security, Biomed, and executive needs, Medigate deploys and scales effortlessly no matter the user or use case.
Integrates seamlessly with your existing tech stack
Medigate's extensive technical ecosystem integrations empower you to easily extend your existing security infrastructure to your healthcare environment.
Staff Awareness, HIPAA, & Phishing Training
Security Awareness & Phishing Training
PatientLock's Security Awareness Training and Phishing Testing service utilizes best-in-class KnowBe4 to combine continuous training and simulated testing of users, while satisfying regulatory compliance such as HIPAA, PCI, and SOX mandates.
In addition to KnowBe4, the PatientLock security awareness training program is built specifically to satisfy healthcare regulatory and compliance requirements for awareness training. Our services are constantly updated to ensure your users are being exposed to the latest phishing techniques, and training content is customized for different at-risk groups such as privileged users, physicians and staff, executives, and IT-resources.
We integrate current threat intelligence and real-time attack profiles into training and testing based on the most current social engineering tactics being used by attackers. Our "real-life" social engineering tests (hacks) are performed throughout the year and simulate the real tactics and techniques hackers are leveraging, exposing users to real life scenarios in a simulated environment
before falling victim to real threats.
PatientLock experts will help you build a custom security awareness training program that considers desired testing frequency, internal department factors, risk profiles and any custom tests specific to your healthcare organization.
PatientLock manages the entire security awareness program to
Work with the customer to develop a custom security awareness training schedule
Build an Interactive training program from over 100 different online courses
Work with customers to post policies that need annual sign offs
Provide a training portal for users to log in and track training progress
Administer Monthly/Quarterly security topic of the month campaigns
Work with customers to send reminders to users who are delinquent on training
Provide content like posters and signs that can be displayed in breakrooms
Run special events around Security Awareness month in October
PatientLock manages the entire social engineering program to include:
Work with the customer to develop and initial test schedule
Perform initial onboarding and user setup
Provide a baseline of user security awareness testing to help measure the current state of security awareness
Perform initial validation testing of your email security controls
Incorporate industry threat intel, tactics, and trends into a custom quarterly phishing campaign
Administer quarterly phishing simulation tests
Provide reinforcement training to any failed users that failed testing
Provide reports and dashboards specific to testing outcomes
Hold quarterly review sessions with the customer to assess testing metrics
Perform quarterly performance reviews and provide suggested program improvements
Powered By

Leveraging Industry-best KnowBe4
One of your greatest security risks is your own workforce. Employee behavior, though unintentional, can put your organization at risk. In 2021, 44% of security incidents were caused by employees falling victim to phishing scams. But employees can actually be your best defense. Learn how to harden your human defenses, curb risky behavior, and reinforce employees’ recognition of common tactics.
Security Awareness & Phishing Training
PatientLock's Security Awareness Training and Phishing Testing service utilizes best-in-class KnowBe4 to combine continuous training and simulated testing of users, while satisfying regulatory compliance such as HIPAA, PCI, and SOX mandates.
In addition to KnowBe4, the PatientLock security awareness training program is built specifically to satisfy healthcare regulatory and compliance requirements for awareness training. Our services are constantly updated to ensure your users are being exposed to the latest phishing techniques, and training content is customized for different at-risk groups such as privileged users, physicians and staff, executives, and IT-resources.
We integrate current threat intelligence and real-time attack profiles into training and testing based on the most current social engineering tactics being used by attackers. Our "real-life" social engineering tests (hacks) are performed throughout the year and simulate the real tactics and techniques hackers are leveraging, exposing users to real life scenarios in a simulated environment
before falling victim to real threats.
PatientLock experts will help you build a custom security awareness training program that considers desired testing frequency, internal department factors, risk profiles and any custom tests specific to your healthcare organization.
PatientLock manages the entire security awareness program to
Work with the customer to develop a custom security awareness training schedule
Build an Interactive training program from over 100 different online courses
Work with customers to post policies that need annual sign offs
Provide a training portal for users to log in and track training progress
Administer Monthly/Quarterly security topic of the month campaigns
Work with customers to send reminders to users who are delinquent on training
Provide content like posters and signs that can be displayed in breakrooms
Run special events around Security Awareness month in October
PatientLock manages the entire social engineering program to include:
Work with the customer to develop and initial test schedule
Perform initial onboarding and user setup
Provide a baseline of user security awareness testing to help measure the current state of security awareness
Perform initial validation testing of your email security controls
Incorporate industry threat intel, tactics, and trends into a custom quarterly phishing campaign
Administer quarterly phishing simulation tests
Provide reinforcement training to any failed users that failed testing
Provide reports and dashboards specific to testing outcomes
Hold quarterly review sessions with the customer to assess testing metrics
Perform quarterly performance reviews and provide suggested program improvements
Powered By

Security Awareness & Phishing Training
PatientLock's Security Awareness Training and Phishing Testing service utilizes best-in-class KnowBe4 to combine continuous training and simulated testing of users, while satisfying regulatory compliance such as HIPAA, PCI, and SOX mandates.
In addition to KnowBe4, the PatientLock security awareness training program is built specifically to satisfy healthcare regulatory and compliance requirements for awareness training. Our services are constantly updated to ensure your users are being exposed to the latest phishing techniques, and training content is customized for different at-risk groups such as privileged users, physicians and staff, executives, and IT-resources.
We integrate current threat intelligence and real-time attack profiles into training and testing based on the most current social engineering tactics being used by attackers. Our "real-life" social engineering tests (hacks) are performed throughout the year and simulate the real tactics and techniques hackers are leveraging, exposing users to real life scenarios in a simulated environment
before falling victim to real threats.
PatientLock experts will help you build a custom security awareness training program that considers desired testing frequency, internal department factors, risk profiles and any custom tests specific to your healthcare organization.
PatientLock manages the entire security awareness program to
Work with the customer to develop a custom security awareness training schedule
Build an Interactive training program from over 100 different online courses
Work with customers to post policies that need annual sign offs
Provide a training portal for users to log in and track training progress
Administer Monthly/Quarterly security topic of the month campaigns
Work with customers to send reminders to users who are delinquent on training
Provide content like posters and signs that can be displayed in breakrooms
Run special events around Security Awareness month in October
PatientLock manages the entire social engineering program to include:
Work with the customer to develop and initial test schedule
Perform initial onboarding and user setup
Provide a baseline of user security awareness testing to help measure the current state of security awareness
Perform initial validation testing of your email security controls
Incorporate industry threat intel, tactics, and trends into a custom quarterly phishing campaign
Administer quarterly phishing simulation tests
Provide reinforcement training to any failed users that failed testing
Provide reports and dashboards specific to testing outcomes
Hold quarterly review sessions with the customer to assess testing metrics
Perform quarterly performance reviews and provide suggested program improvements
Powered By

24/7/365 Security Operations Center
Enterprise-class monitoring at an affordable price
With today’s threat landscape and risk to healthcare organizations, monitoring the perimeter with a firewall is no longer enough. Organizations of all sizes need to monitor all points in their clinic, hospital, or healthcare related business. That means networks, servers, databases, people, connected medical devices, and traditional endpoints.
That’s a challenge for already strained IT (or IS) resources.
PatientLock solves that challenge by acting as a force multiplier to a healthcare organization’s security staff by monitoring network assets, 24x7x365. PatientLock monitors your environment around-the-clock, neutralizing threats before they can impact your business or patients.
Extended Detection and Response (XDR)
A Silo-Breaking, Game Changing Solution
Industry-leading extended detection and response utilizes 250+ analytic behavioral detections to give you a fully managed, end-to-end security solution.
Change from reactive to proactive security. Specializing in finding what other products miss, our industry-leading Extended Detection and Response solution leverages a combination of artificial intelligence, machine learning, and behavioral analytics, to proactively identify sophisticated threats before they happen.
Managed Detection & Response (MDR)
Secure Your Business with Simple, Affordable Enterprise-grade Protection
Clinical information systems (EMRs) and the widespread use of email and telehealth platforms has created massive attack surface. Risk is everywhere in the modern healthcare environment, so it’s critical that you protect your business and patients. Unfortunately, common cybersecurity challenges faced by healthcare organizations can be barriers to your success.
PatientLock Managed Detection and Response (MDR) eliminates barriers to better information security. Designed to force-multiply existing IT or IS resources, PatientLock’s managed-services model makes protecting modern healthcare environments possible, delivering effective cybersecurity protection designed to fit any healthcare business, or budget.
Managed Endpoint Detection & Response (EDR)
Featuring SentinelOne’s Singularity Complete
From laptops and desktops to servers and mobile devices, endpoints expose healthcare organizations to sophisticated threats. Organizations have their work cut out for them, balancing an escalating number of endpoints with effective threat protection across the digital environment. Endpoints are a major entry point for disruptive threats. Legacy anti-virus and endpoint protection programs simply aren’t responsive enough to stop modern attacks.
By layering 24/7/365 managed detection and response (MDR) over SentinelOne’s Singularity Complete, PatientLock makes it simple to defend against endpoint risk.
Email Protection Services
Proactive Protection for Healthcare’s Most Vulnerable System
Email is now a core tool used for business and patient communication. It’s also the number one attack vector.
PatientLock Email Protection Services (EPS) provides 24/7/365 proactive protection for your most critical – and most vulnerable system.
PatientLock Email Protection Services (EPS) makes it simple to defend against email threats, ensure business continuity, and satisfy compliance and audit obligations. Whether you need protection for your existing, on-prem, cloud-based, or hybrid email solution, PatientLock simplifies email protection.
Multi-Factor Authentication (MFA)
Scalable Access Security That’s Simple and Powerful
Get secure access for any user and device to any environment, from anywhere.
The shift to hybrid work models and perimeterless environments amplifies the need for security to shift too. Today, your data and applications no longer sit behind a corporate firewall – and neither do your users.
You need assurance that only the right users and secure devices are accessing your applications and systems every time.
The use of strong authentication increases your security, but not all solutions are the same. Cost, flexibility, and the complexity of deployment and use can vary across solutions.
Managed Firewall
Reveal Hidden threats with PatientLock
The PatientLock Web Application Firewall (WAF) service protects your web-based applications from attack by monitoring input, output and access attempts, and blocking any malicious activity.
When attacks are detected, the Web Application Firewall alerts analysts in our Security Operations Centers (SOCs) immediately block the originating IP address. The service protects against the full range of application vulnerabilities including cross-site scripting (XSS), injection flaws (SQL, LDAP, Xpath and others), malicious file execution, insecure direct object references, cross-site request forgery (CSRF), information leakage and improper error handling, broken authentications and session management, insecure cryptographic storage, insecure communications, and failure to restrict URL access threats more quickly.
Vulnerability Management
Scanning + Remediation Advice
Most companies scan for vulnerabilities. But scans alone do not eliminate the issues or reduce your risk; they simply identify the vulnerabilities – and often in large numbers.
Not all pose risk to your business. And we can help you determine – and address – the ones that do.
PatientLock Vulnerability Management takes the complexity out of detecting, prioritizing, and remediating issues in your environment. We deliver the skilled resources, processes, and technology needed to manage the full vulnerability life cycle – helping you find and fix potential exposures before they can be exploited.
IoMT Security
Protecting Connected Medical Devices with Medigate
Unlike connected devices in traditional Internet of Things (IoT) deployments, attacks on devices in the Internet of Medical Things (IoMT) can have fatal consequences for patients, as well as devastating implications for healthcare providers’ reputations. Protecting connected medical devices poses several unique challenges that traditional IoT security solutions cannot address.
Staff Awareness, HIPAA, & Phishing Training
Leveraging Industry-best KnowBe4
One of your greatest security risks is your own workforce. Employee behavior, though unintentional, can put your organization at risk. In 2021, 44% of security incidents were caused by employees falling victim to phishing scams. But employees can actually be your best defense. Learn how to harden your human defenses, curb risky behavior, and reinforce employees’ recognition of common tactics.
